Microsoft Copilot Studio
Customize Copilot and Build AI Apps & Bots
Secure Microsoft Copilot Studio and enable anyone to customize Copilot for M365 and/or build their own copilots, bots, and GPTs using a no-code approach


The pROBLEM
Implement control without stifling innovation
Copilot Studio serves as both the extension framework for Microsoft Copilot, and also a way for anyone to build their own AI apps and bots, creating a vast attack surface
Lack of Visibility
With the average enterprise developing ~2600 of their own copilots, keeping up with the business context for each one is a tall order
Data Leakage
User-built bots and copilots are often under-authenticated, over-provisioned, and contain hard-coded secrets; a recipe for data leakage
Prone to Prompt Injection
AI apps and copilots can easily be tricked by bad actors into sharing too much information
Remote Copilot Execution
When bots are shared on the public internet, hackers can perform RAG poisoning and fuzzing attacks to steal your data
The solution
Enable anyone to securely build their own copilots
Copilot Studio offers some of the most exciting capabilities for professional and citizen developers, the Zenity platform solves for the biggest risks
Continuous Visibility
Identify all copilots, bots, and AI apps that are built within Microsoft Copilot Studio
Assess for Risk
Identify AI apps and copilots that are internet-facing and can access your data
Govern with Confidence
Prevent RAG poisoning and indirect prompt injection leading to RCE attacks
Understanding where risks lie is always the first step; run your own risk assessment today!
What’s needed to secure Copilot Studio?
Zenity provides the only AISPM solution on the market that helps to secure and govern development happening on Copilot Studio. Understanding where risks lie is always the first step; run your own risk assessment today!
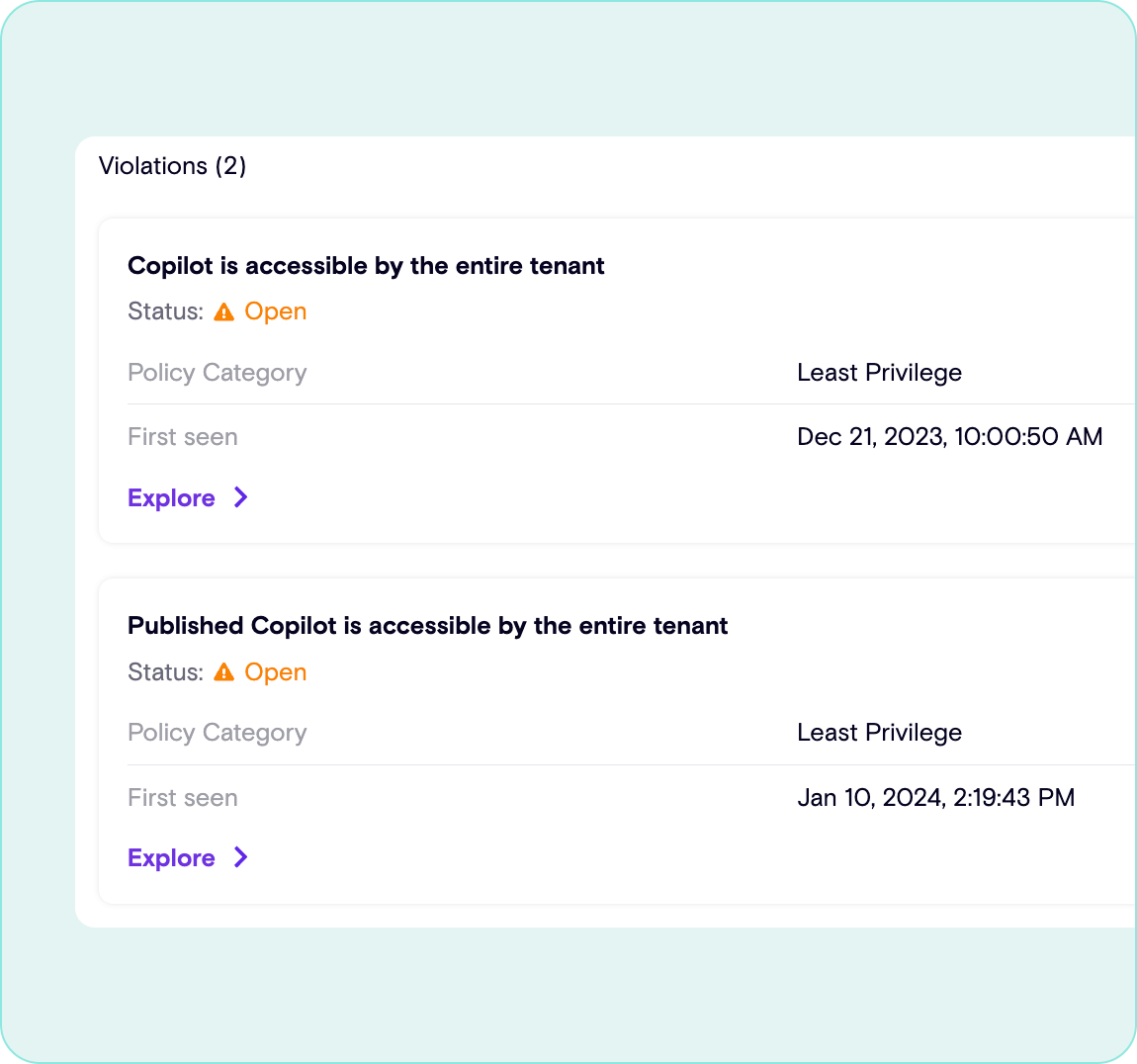
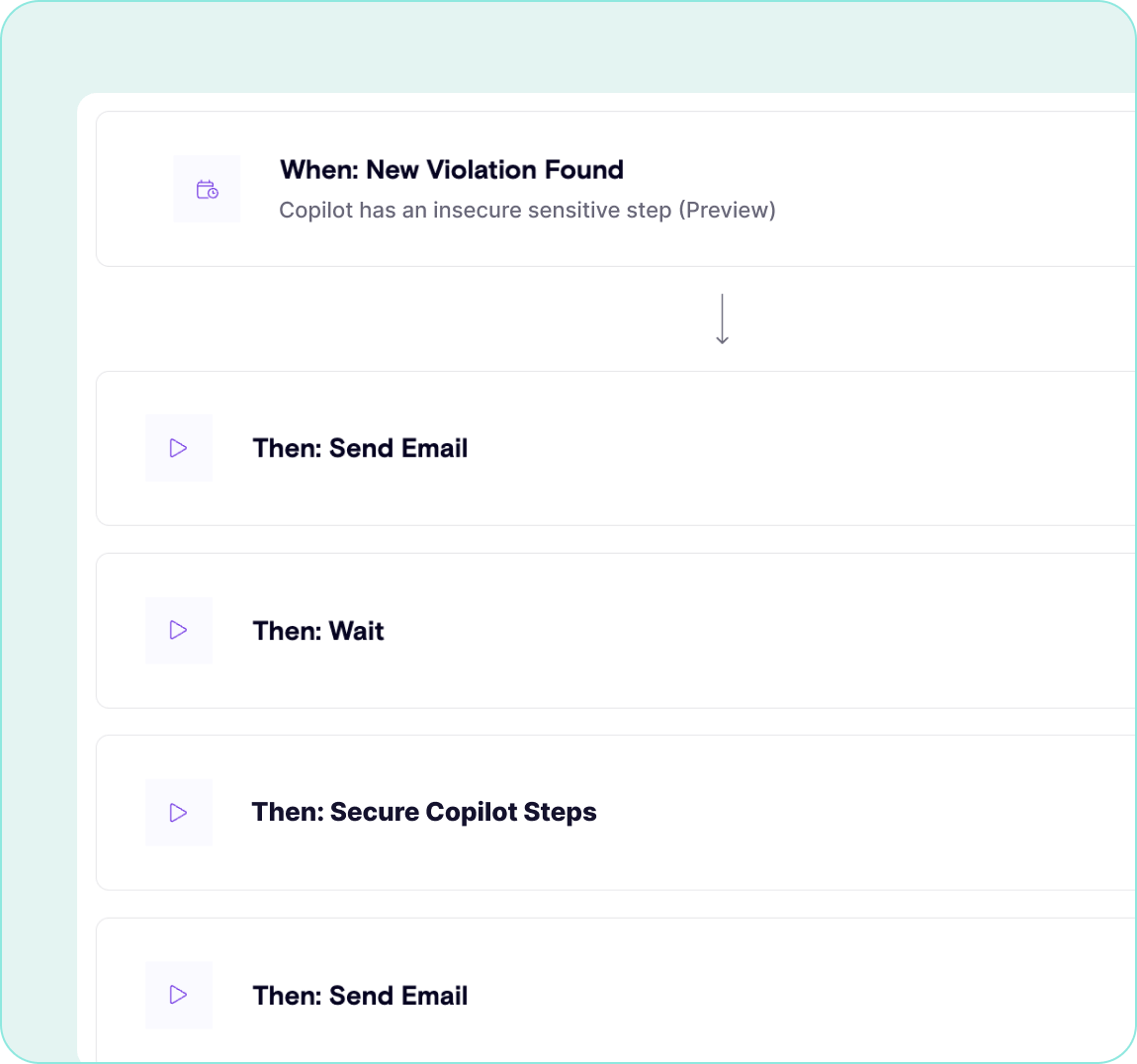
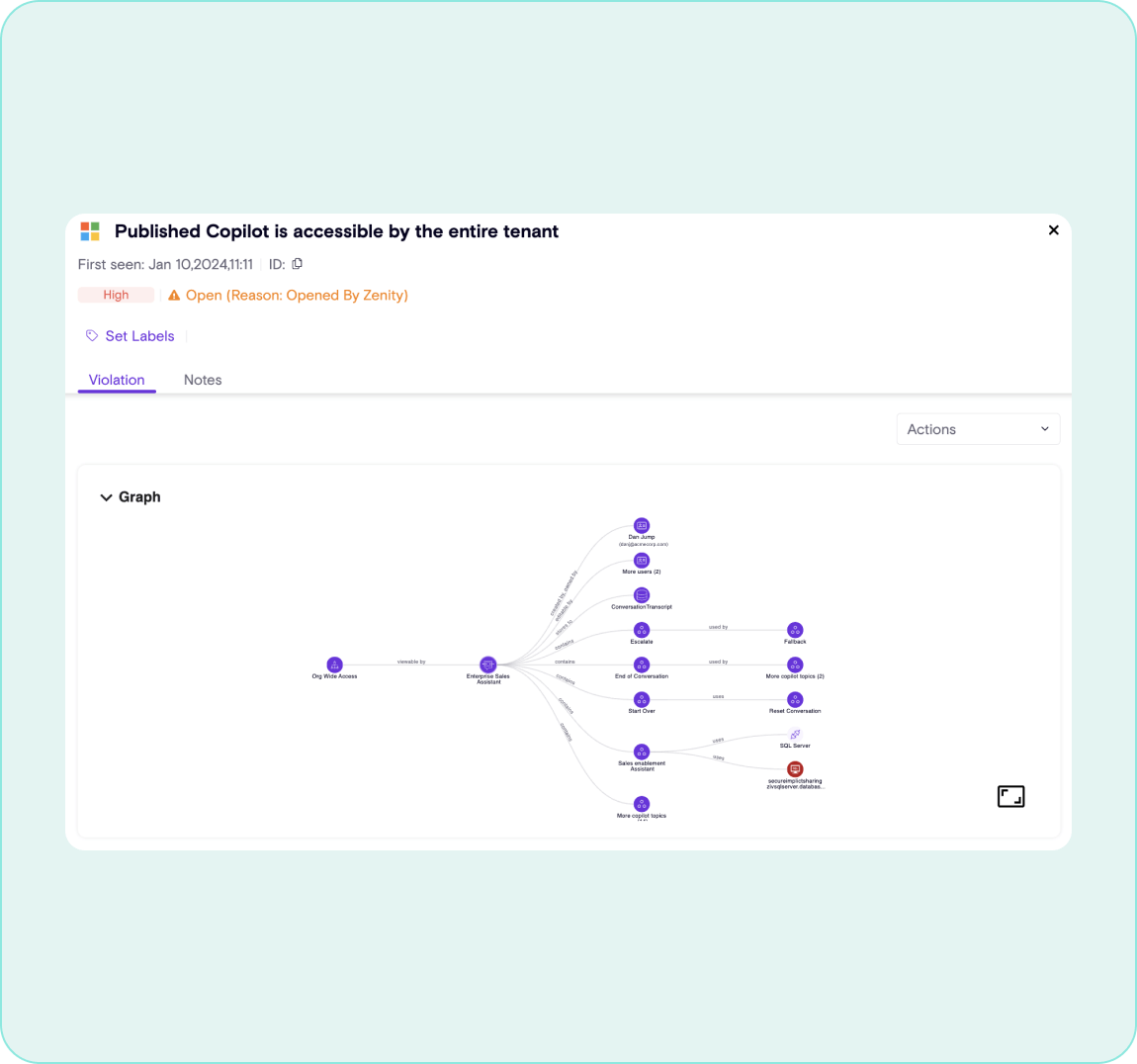
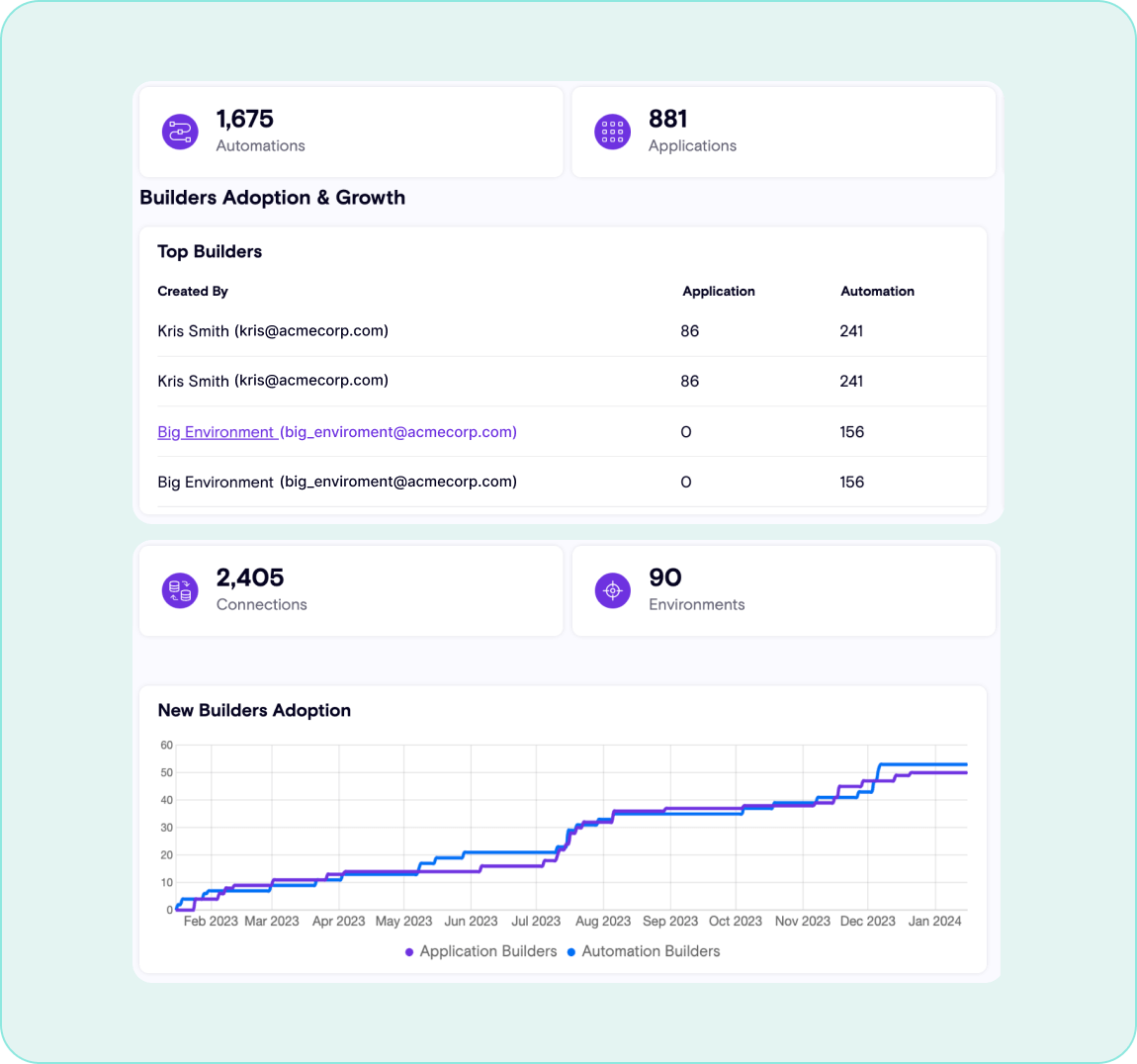

Identify Data Leakage
Find which copilots have access to corporate data first, then determine who has access to use or interact with that copilot

Prevent Remote Copilot Execution
Detect RAG poisoning and neutralize hidden instructions before they can impact copilot conversations

Prevent Prompt Injection
Detect jailbreak and prompt injection attacks in real-time to ensure copilots work for you, not against you

Empower End Users
Confidently unleash Copilot Studio capabilities to all users knowing that Zenity has your back
Want to assess your risk?
If you’re looking to kickstart your enterprise copilot security program, schedule a free assessment now!