Power platform
Leverage Power Platform to the Max with Strong Security
With Power Apps, BI, Flows, and Automate, it has never been easier for professional and citizen developers to build power applications. But what about security and governance?


The pROBLEM
Taking security and governance to the next level
Zenity brings deep security and governance to Power Platform to enable enterprises to take advantage of the powerful suite of development tools
Shared Responsibility
Much like public cloud vendors, Microsoft secures Power Platform services, but not your data or the resources built on top
CoE is just a Start
The CoE is a toolkit that helps organizations get started, but the massive scale of AI-led development introduces a big challenge
Guest Access
Guest accounts are used to give non-employees the ability to build their own apps, automations, and copilots; but they are hard to govern
DLP Bypass
Power Platform DLP is meant as an allow/block list and covers only part of existing running resources
The solution
Unleash Power Platform development… Securely
Power Platform offers lots of exciting capabilities to business users, but too many security teams can’t keep up. Zenity can help

Visibility at Scale
Continuously maintain inventory of all apps, automations, and flows created throughout Power Platform
Risk and Hygiene Assessment
Call out vulnerabilities to arm security teams with insights to ensure apps are properly secured and used
Real-time Governance
Automatically enforce that all apps are properly authenticated, shared, and accessed throughout the enterprise
Needed capabilities for security and governance
Zenity provides deep, business-level logic and actionable insights to ensure Power Platform is properly secured and governed
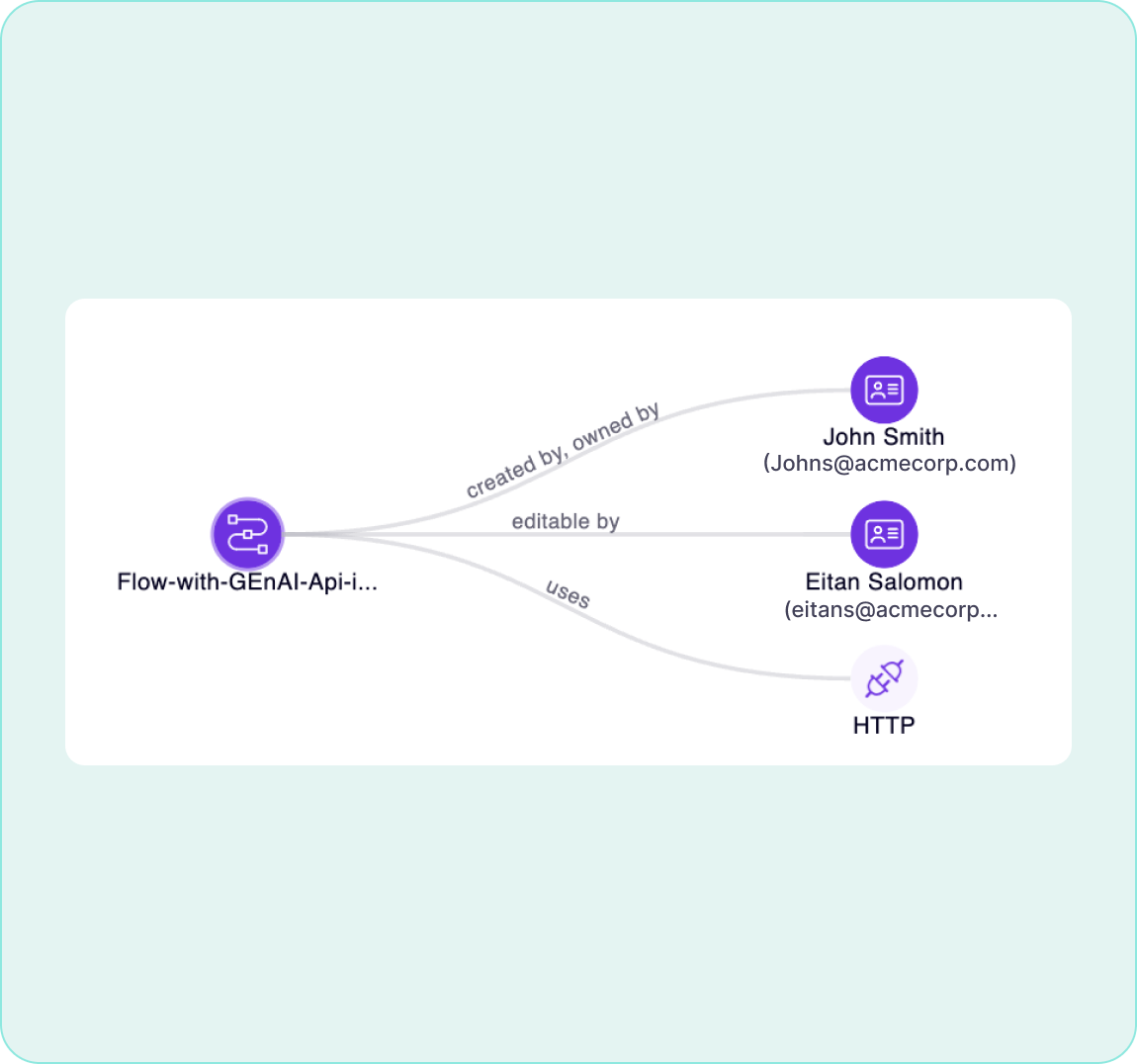
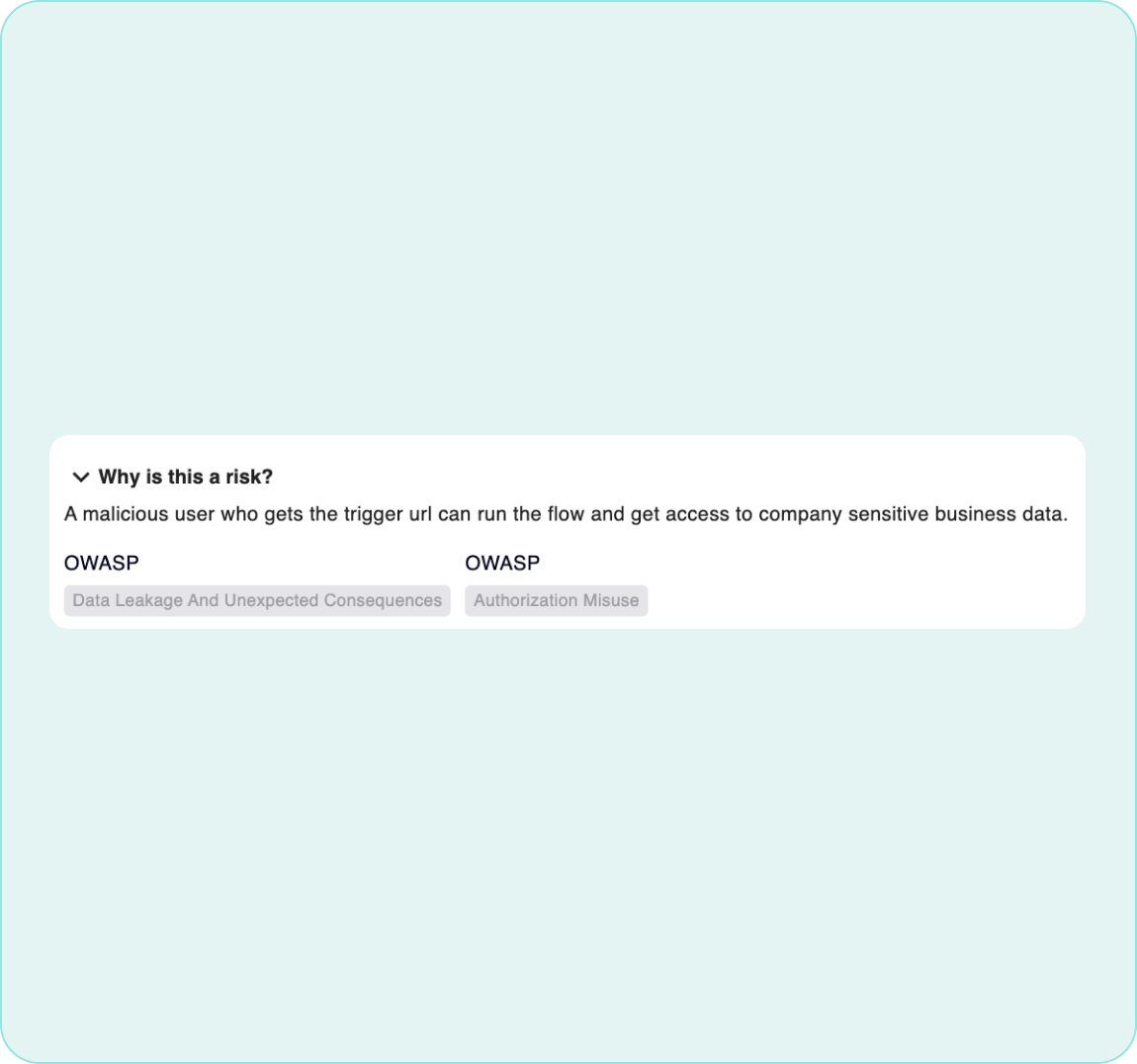
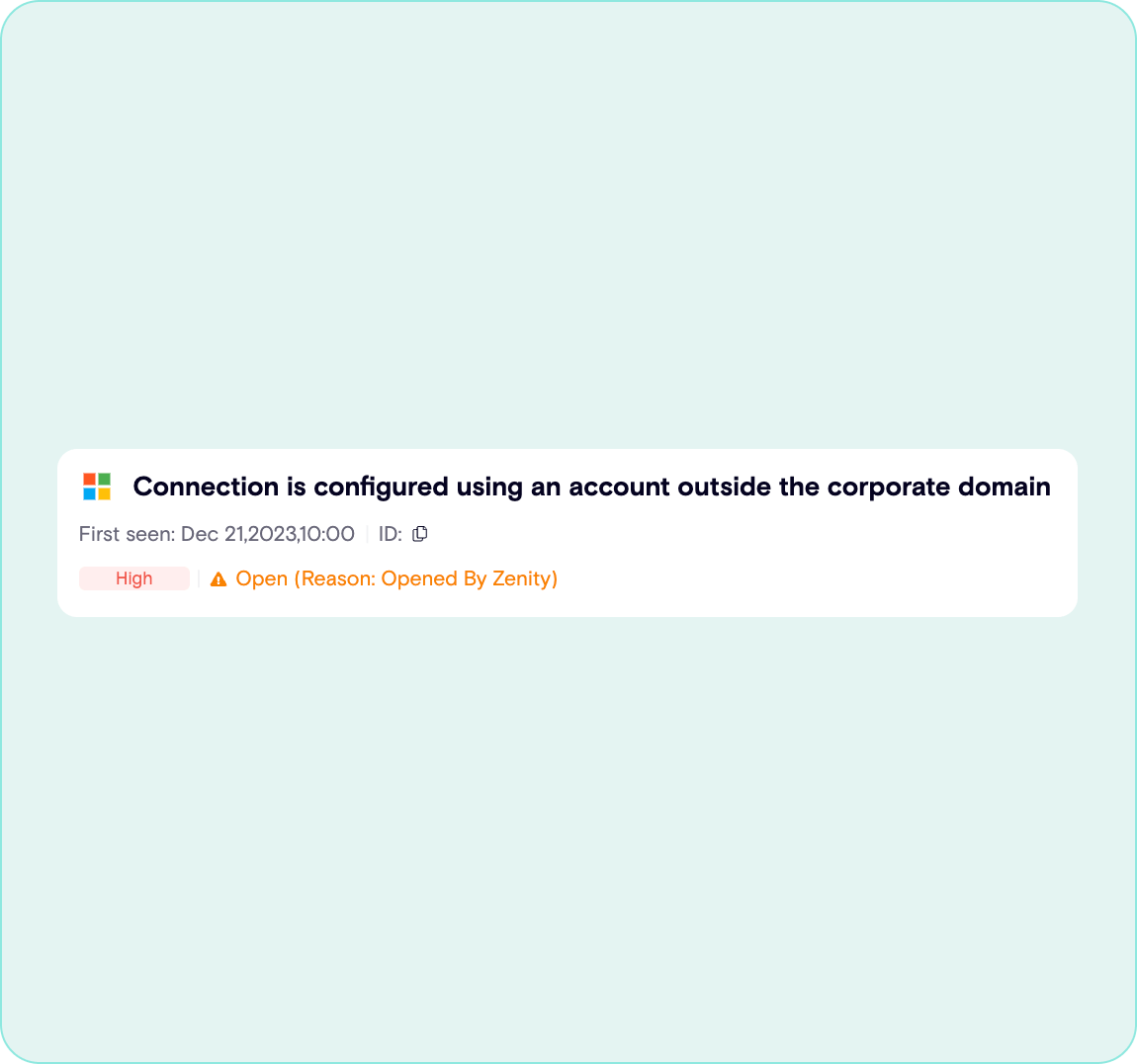
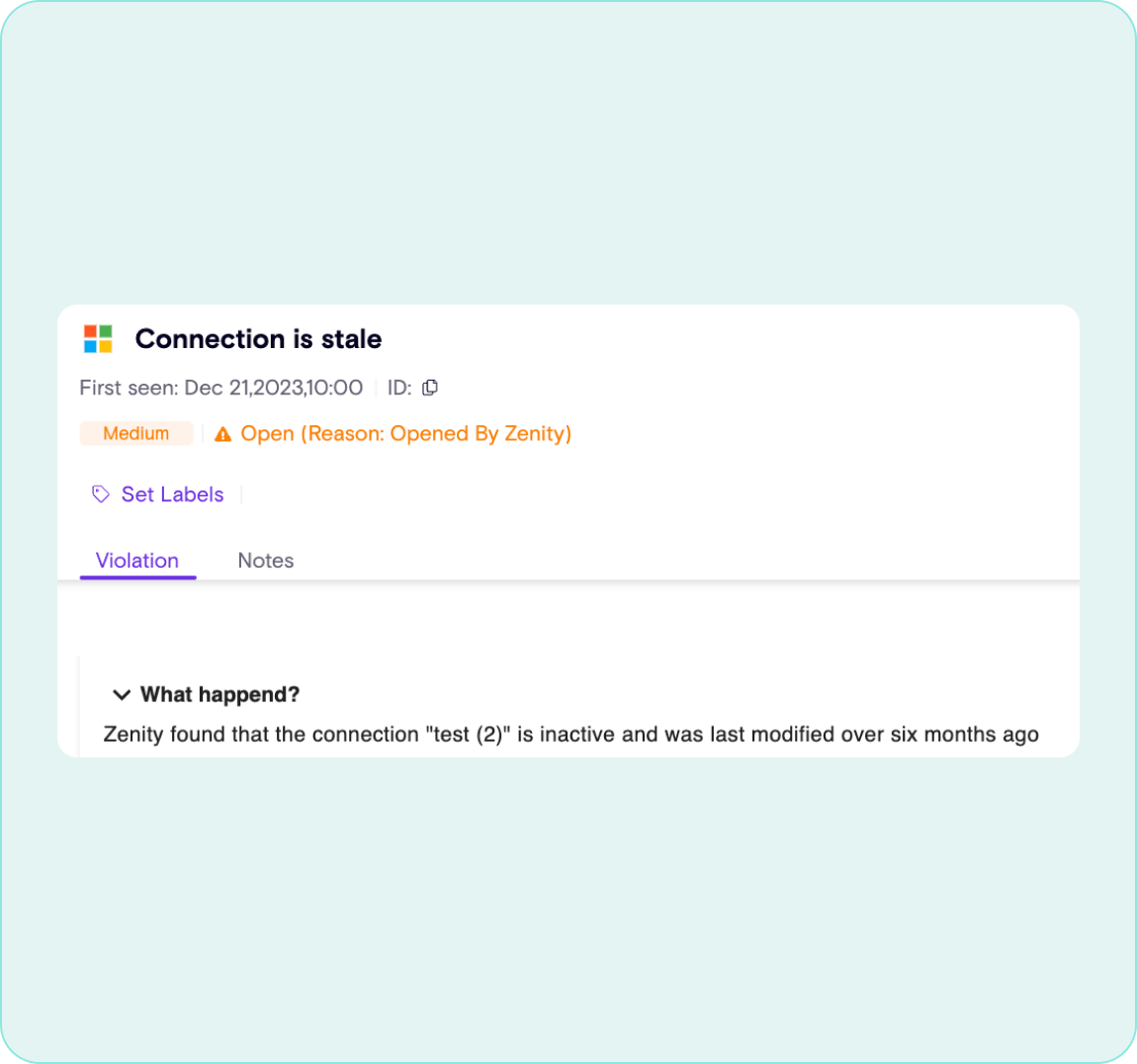

Identify Data and Map Relationships
Apps, automations, flows, and reports do not exist in isolation. Zenity highlights relationships between resources, users, components, and more

Ability to Scale
While the CoE is a good start, it has challenges to scale; Zenity has experience managing some of the largest environments in the world

Remove Excessive Permissions
With Zenity, security teams can remove the risk of hard-coded secrets, label and protect PHI, and prevent oversharing

Maintain Order and Reduce Costs
Zenity highlights unused or unowned apps, helping to reduce unnecessary costs for ‘active’ resources in production and eliminating blind spots
Want to learn more?
Subscribe to our monthly newsletter to stay up-to-date on all the latest updates in the world of
low-code/no-code development