Secure Enterprise Copilots in Runtime
- Maintain visibility into AI copilots and agents, including how they are used across the organization
- Detect and prevent suspicious and malicious activities that are leveraging copilots and agents as an attack surface,
- Prevent promptware from getting into your organization
- Granular policy authorization and custom playbooks for continuous security
AI Security Posture Management (AISPM)
- Continuous scanning to identify AI apps, copilots, and plugins that are in use
- Identify which apps are public facing and contain security vulnerabilities
- Detect and prevent apps that are susceptible to RAG poisoning, remote copilot executions (RCEs), and prompt injection attacks
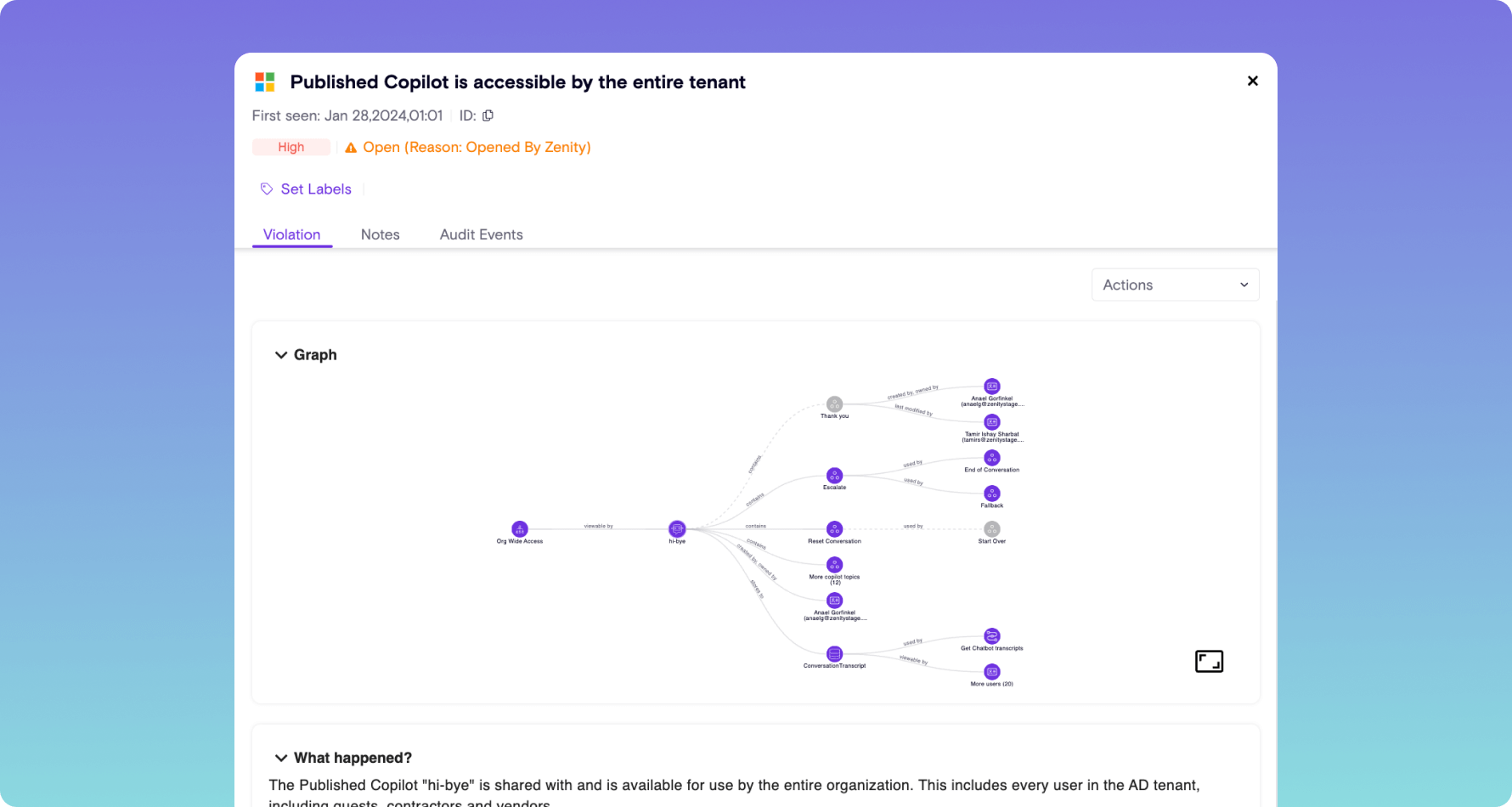
Citizen Development Application Protection Platform (CDAPP)
- Continuous scanning of AI, low-code, and no-code environments
- Assess risk and vulnerabilities for each individual application
- Graph-based visibility and response
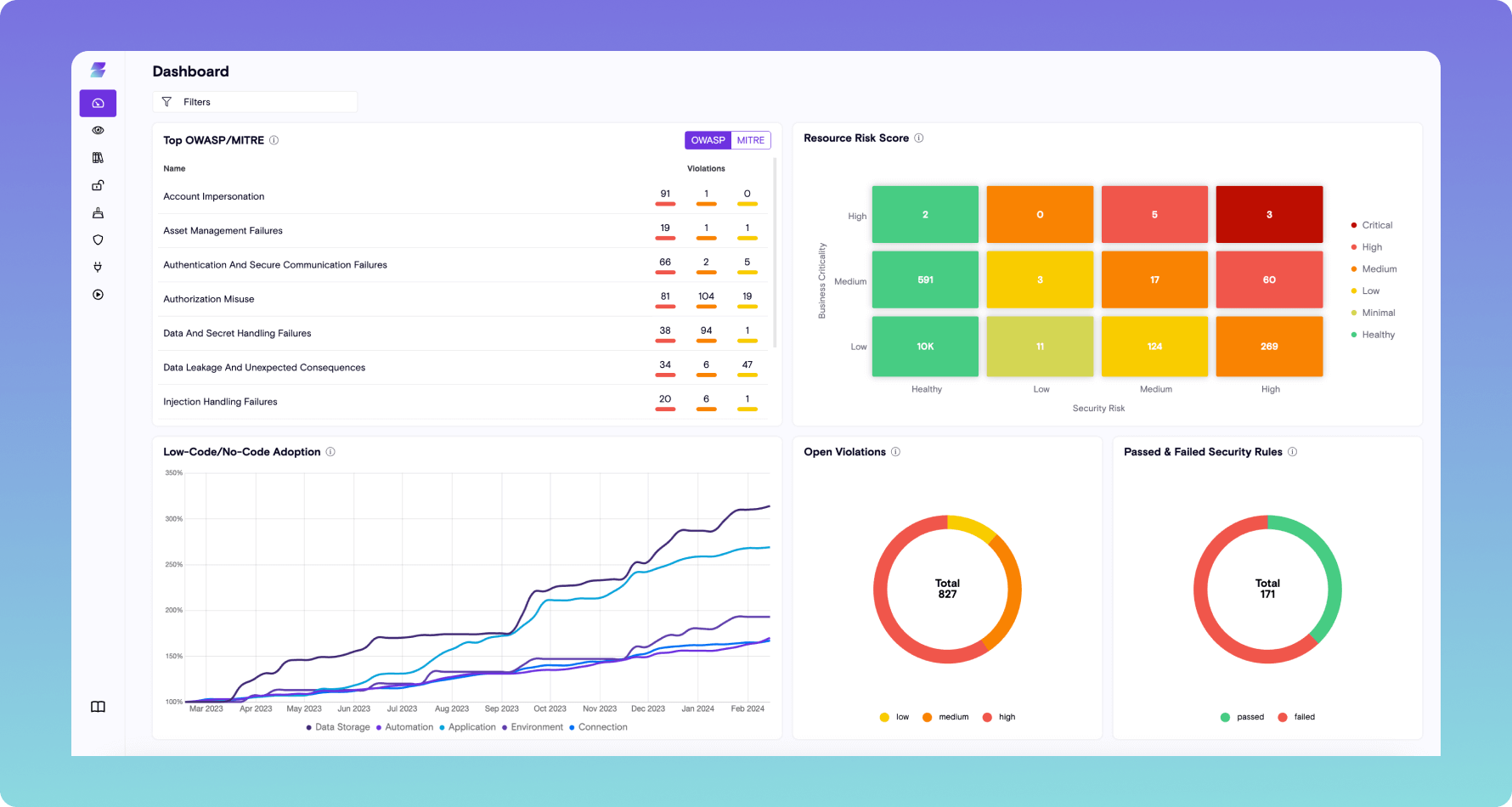
App Security Posture Management (ASPM)
- Centralize visibility and inventory of all copilots and AI applications created across Microsoft, Salesforce, and more
- Implement least privilege to ensure apps are only shared and used by authorized users
- Identify apps that interact with sensitive data and implement guardrails to ensure apps and copilots are in line with corporate policies
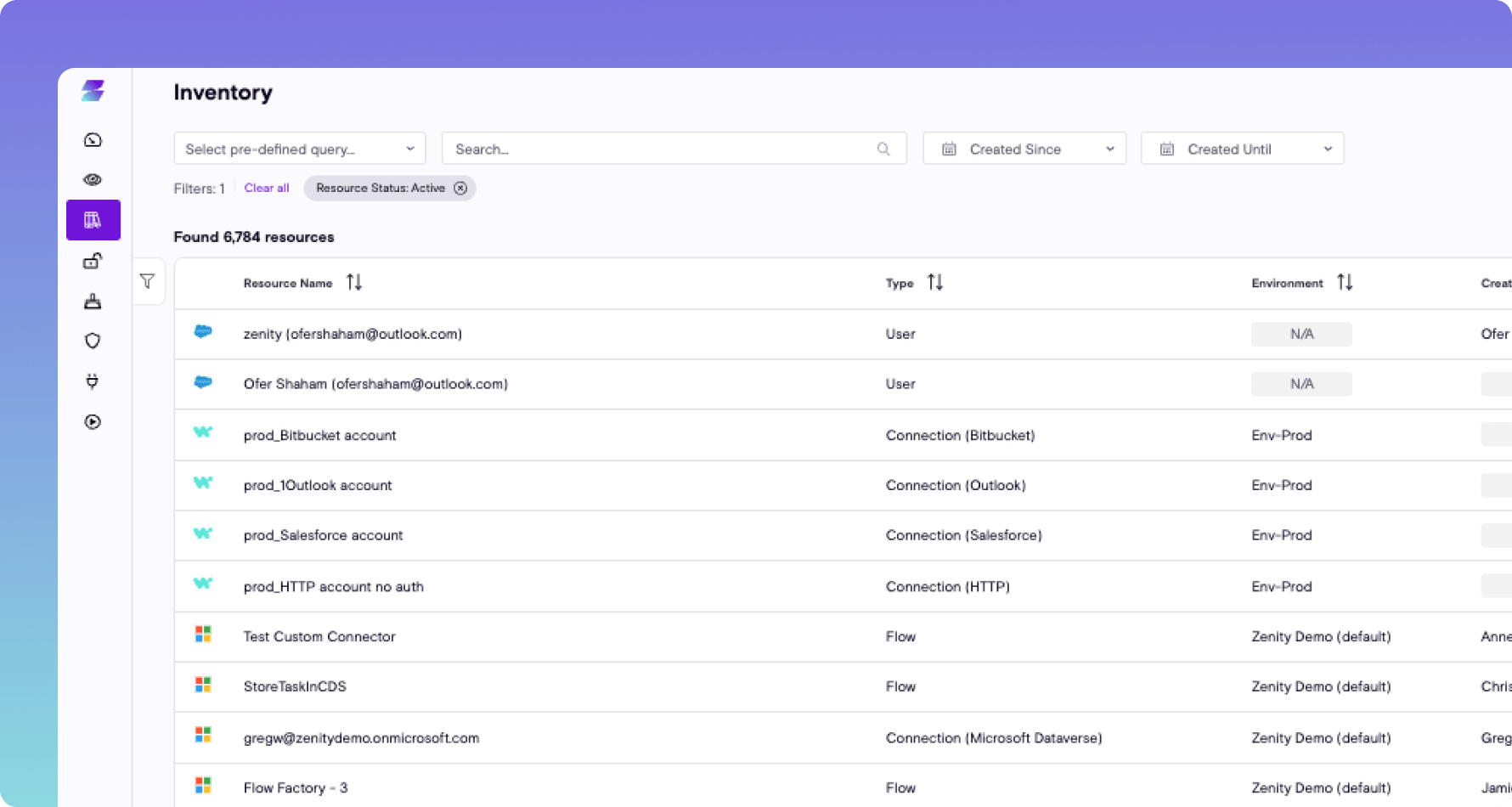
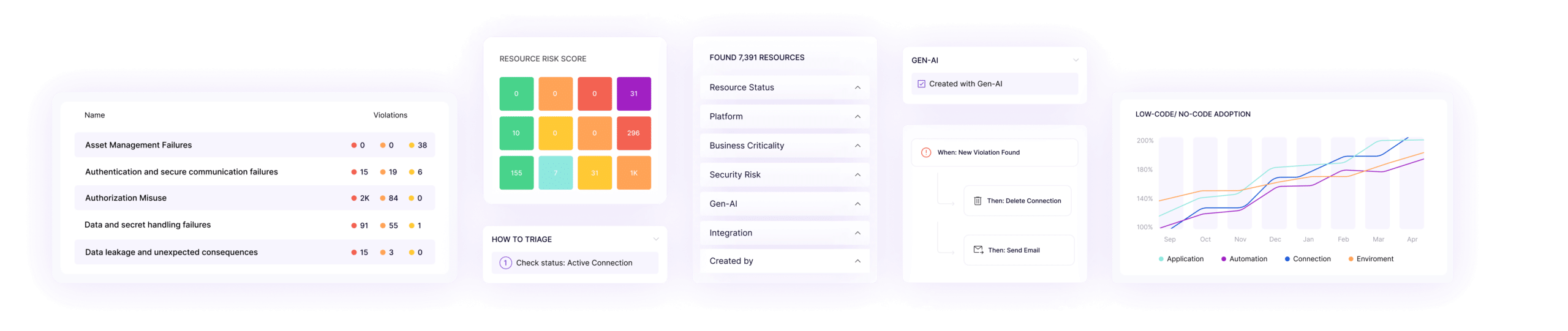
Vulnerability Management
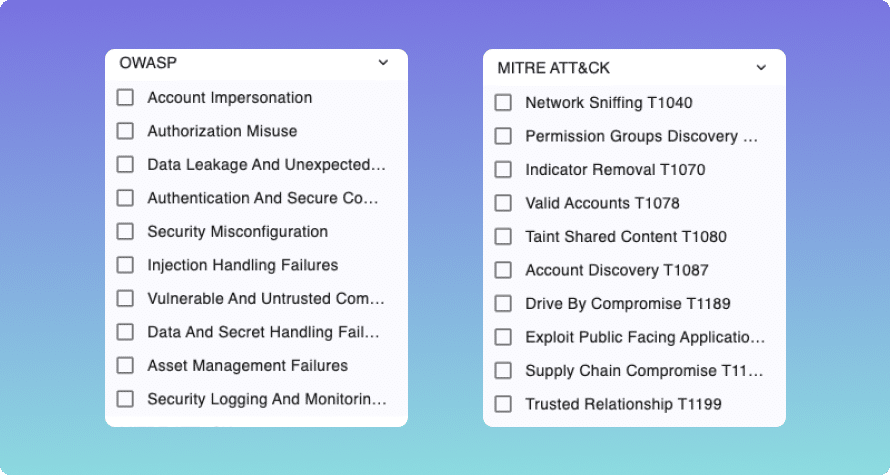
- Scan each individual app, automation, and copilot for risk and map vulnerabilities to OWASP frameworks
- Identify common vulnerabilities like user impersonation, data leakage, credentials sharing, hard-coded secrets, and more
- Flag and mitigate the most critical alerts by combining violations and business context
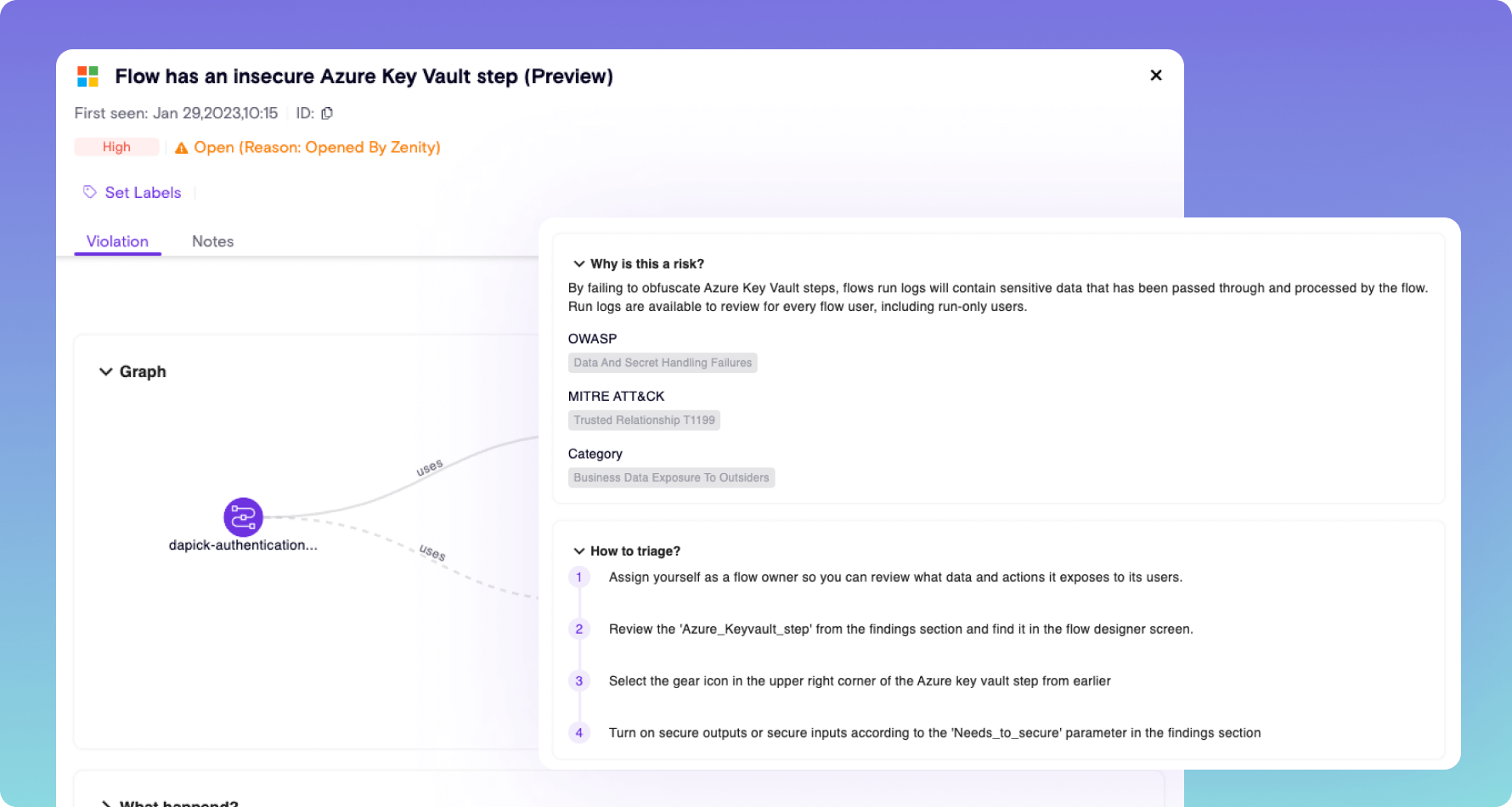
Secrets Scanning
- Identify hard-coded credentials baked into applications as they are built
- Spot insecure steps in how credentials and secrets are retrieved by copilots and low-code apps
- Automate response with playbooks and policies to prevent malicious or unauthorized use
Software Composition Analysis
- Craft robust third-party dependency analysis and SBOM for professional and citizen developed applications and AI copilots
- Identify all third-party components that are used in each individual app, automation, and copilot
- Detect custom code components that are baked into applications and copilots
Data Security Posture Management (DSPM)
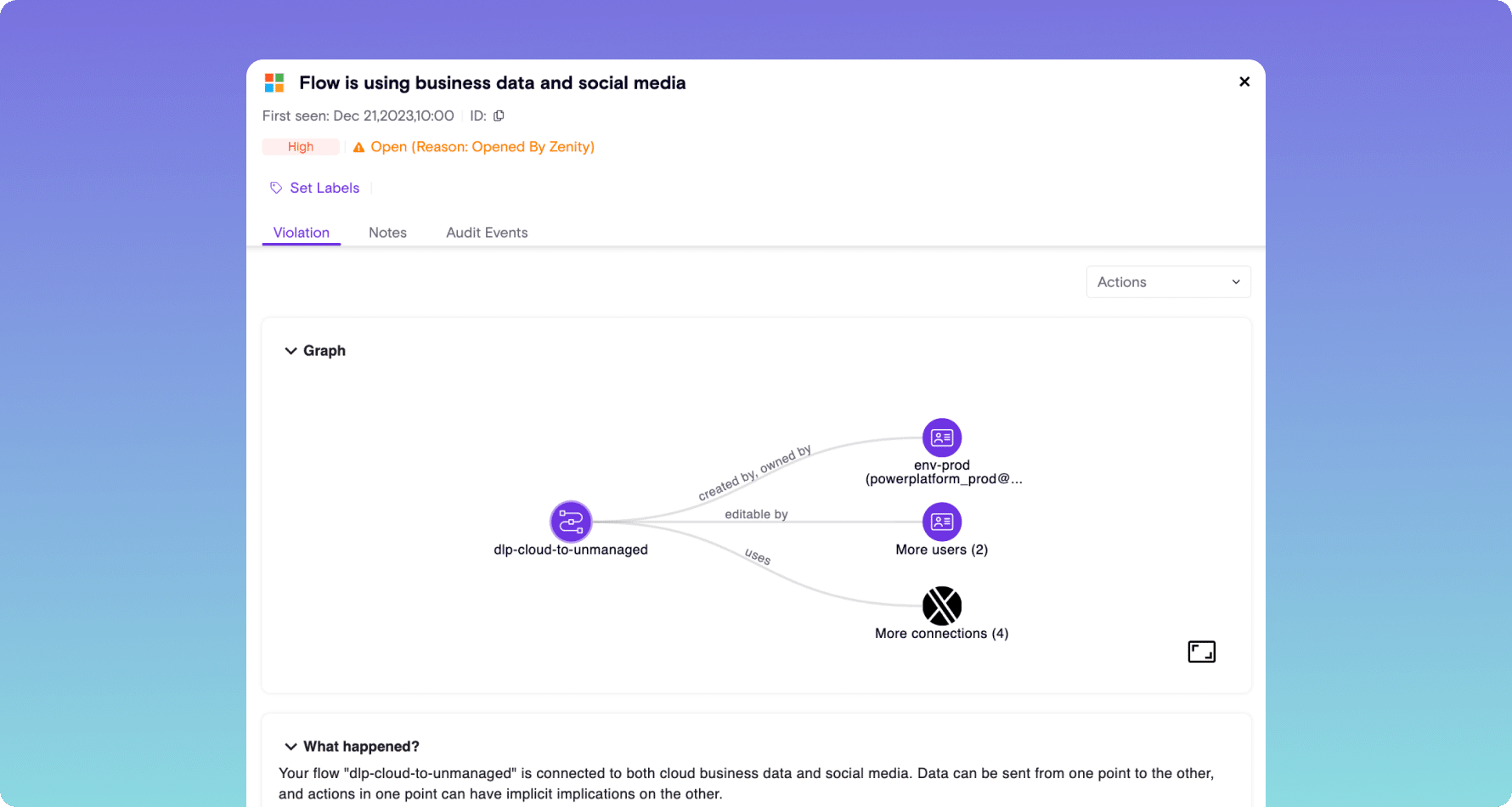
- Analyze all flows to establish what data is taken outside of the corporate environment into personal accounts, external users, etc
- Identify and classify data that each app and copilot interacts with, and tagging information that is labeled as sensitive
- Implement guardrails to prevent apps, automations, and copilots from being built that leak data