New Platform Use Case
Securely Unlock Microsoft 365 Copilot
Microsoft 365 Copilot is extremely powerful, containing access to corporate data, disparate systems, and more. Ensuring it isn’t taken over by RAG poisoning and prompt injection is critical to prevent Remote Copilot Execution (RCE).


The Problem
Real-Time Data Means Real-Time Issues
As enterprises adopt Microsoft 365 Copilot, bad actors can easily manipulate this powerful enterprise copilot and its extensions to gain full control over your enterprise
Lack of Visibility
DLP solutions are not purpose-built to understand the logic behind user / Copilot interactions
RAG Poisoning
As 365 Copilot retrieves data, hackers can take full control of what data and files end users see
Promptware
Bad actors are using malware attack designed for jailbreaking AI apps and copilots that allow them to take over without account compromise
Shadow AI
Business users of all technical backgrounds can interact with and build copilots and agents without IT oversight
The solution
The Zenity AI Trust Layer for Microsoft 365 Copilot
Zenity provides a comprehensive AI Security solution providing real time vulnerability and threat detection, continuous monitoring, embedded control, and automated remediation.
Gain Visibility
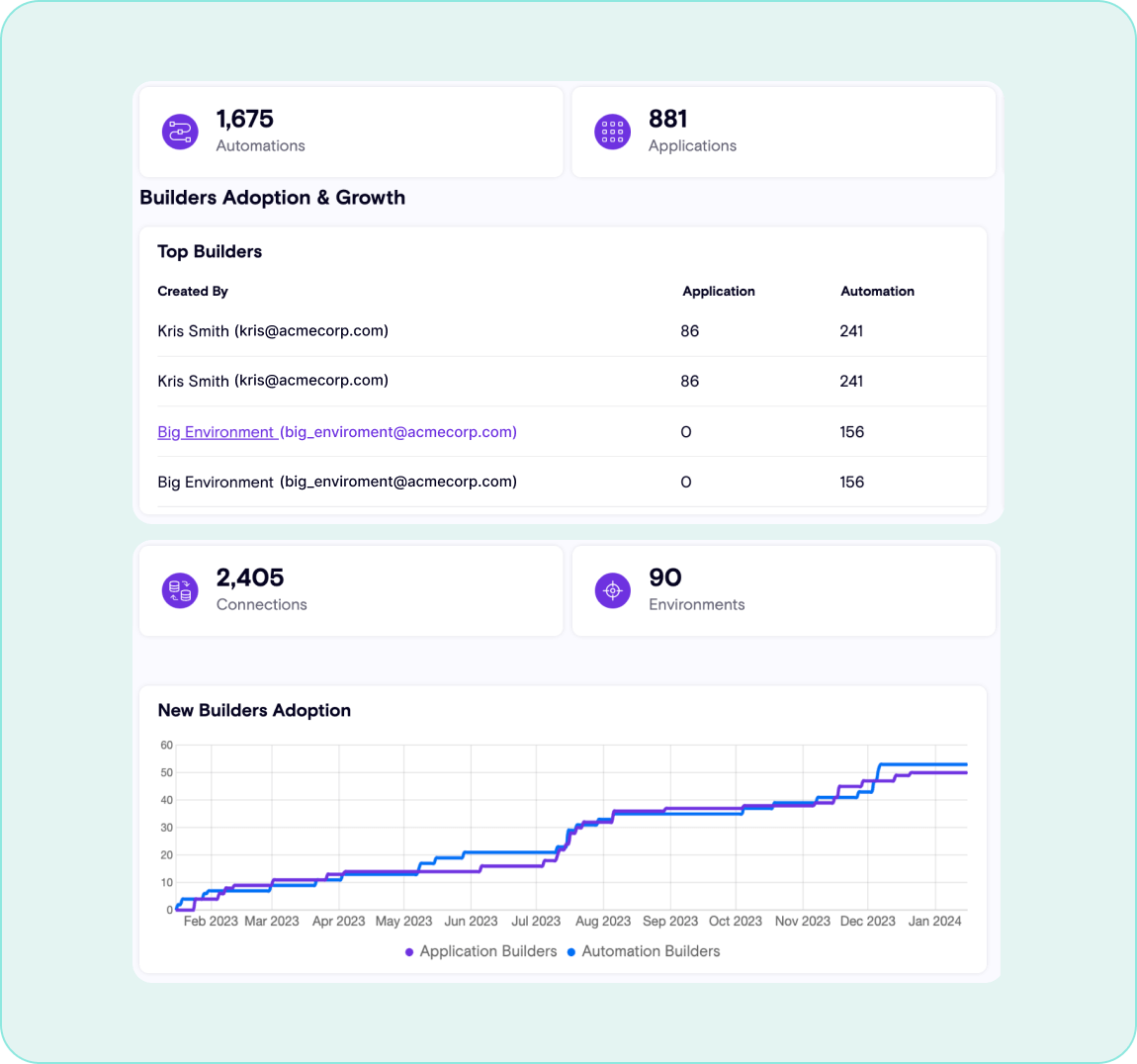
Maintain a continuous inventory for AI copilots and agents, including how they are used across the organization and what risks exist in real-time.
Assess for Risk
Detect and prevent suspicious and malicious activities that are leveraging 365 Copilot as an attack surface, such as data leakage, in runtime
Establish AI Trust Layer
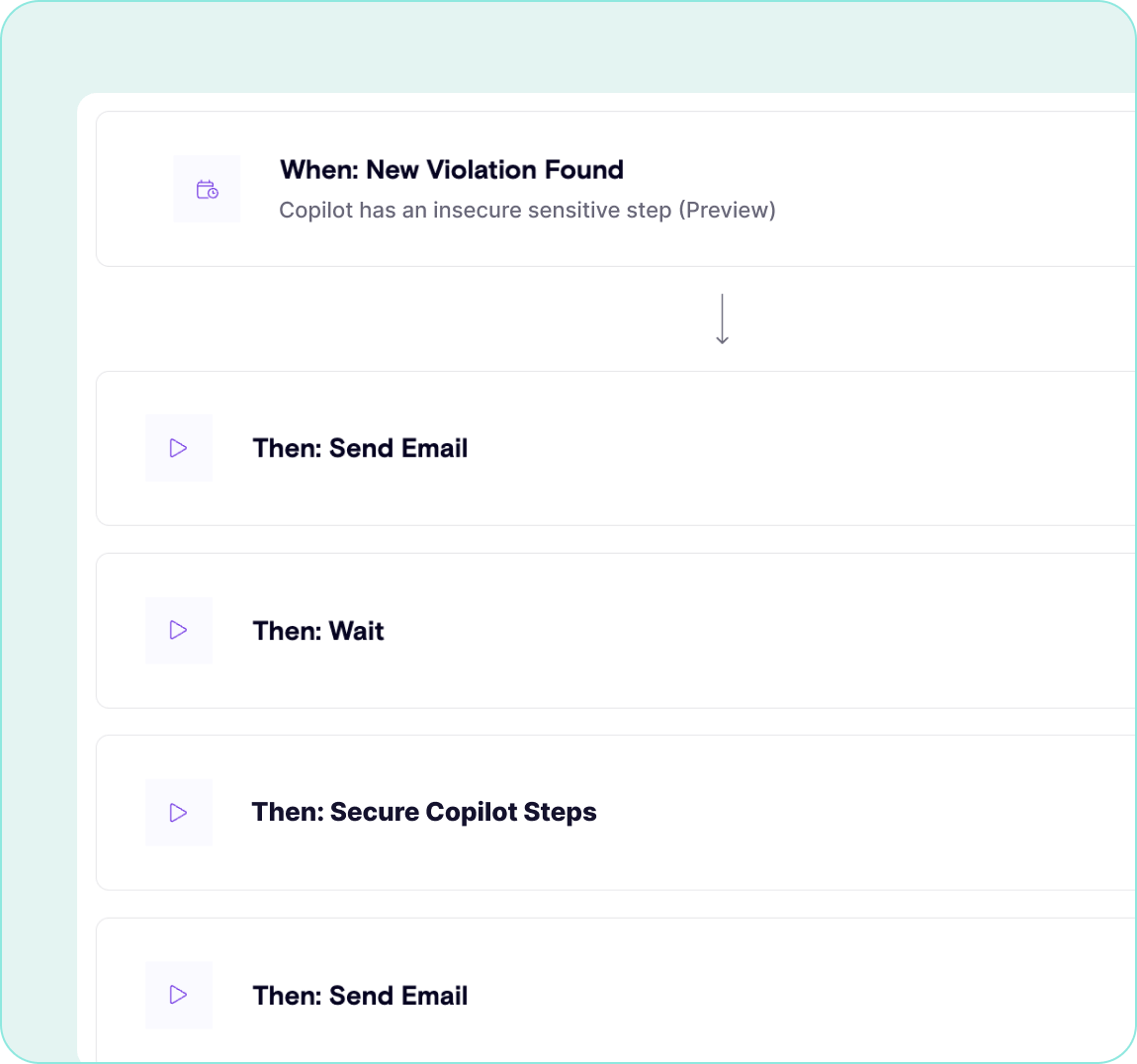
Prevent promptware from getting into your organization and read by 365 Copilot, and automatically respond to detected threats

Prevent Remote Copilot Execution, Unleash Microsoft 365 Copilot
Zenity provides the only agentless AI security solution on the market that helps to secure and govern the end-to-end use of Microsoft 365 Copilot


Understand Interactions
Determine how end users are engaging with Copilot to determine where risks lie and detect prompt injection attacks in real time

Stop Data Leakage
Prevent Remote Copilot Execution by establishing secure guardrails around how Microsoft 365 Copilot is used and who is interacting with it

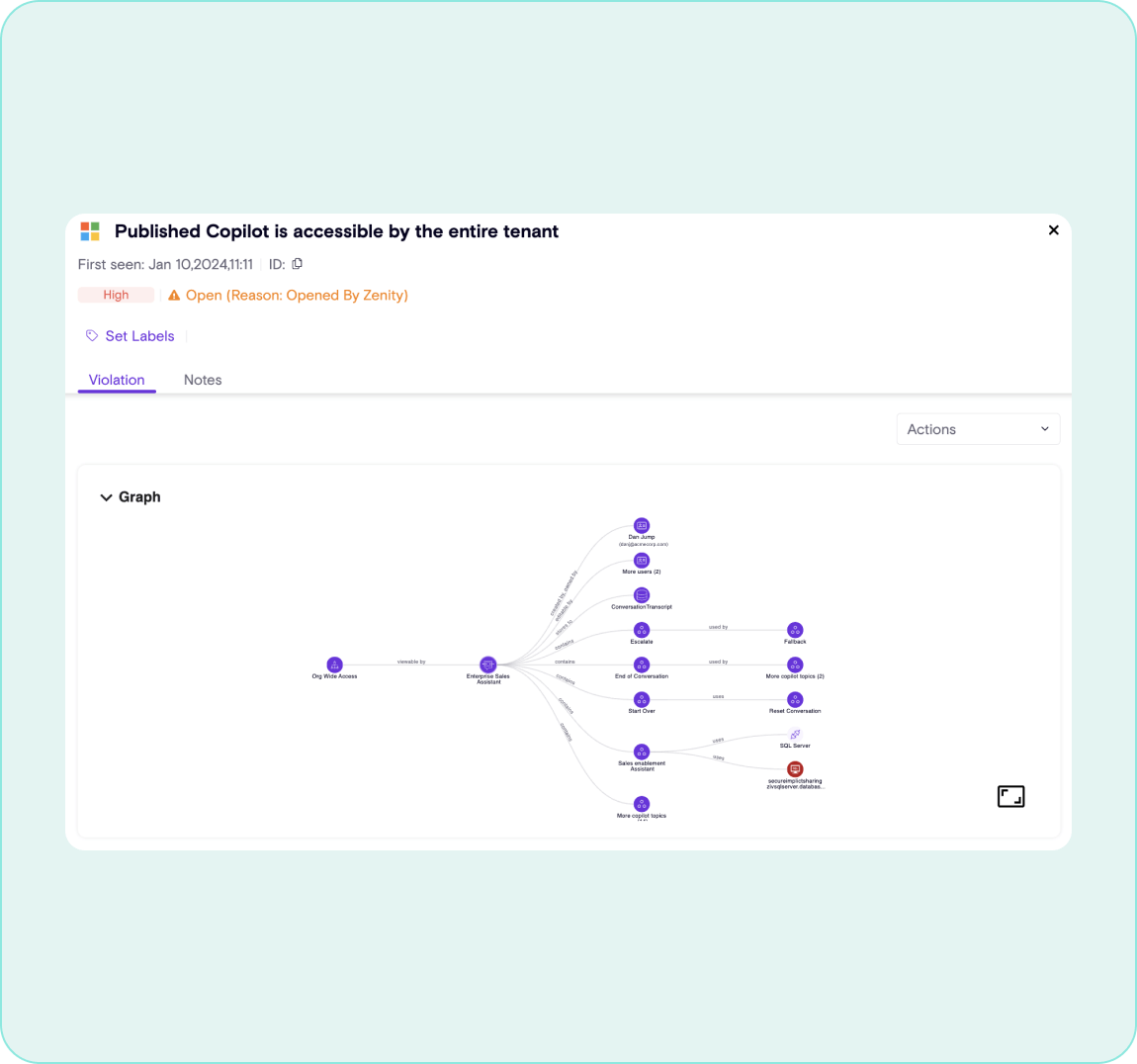
Map Relationships of Plugins
Visualize the composition of each agent, plugin and extension to determine exactly where in the supply chain risks exist and remediate vulnerabilities in real time

Empower End Users
Confidently unlock Microsoft 365 Copilot knowing that AI is not acting against your enterprise, and allow all business users to boost productivity
Want to learn more?
Subscribe to our monthly newsletter to stay up-to-date on all the latest updates in the world of
low-code/no-code development