Business Continuity
Preserve Business Continuity
Business users and developers are building what they need, as they need it. That’s fantastic for your business – so long as you can ensure business continuity

The pROBLEM
More apps means more to account for
Zenity ensures that abandoned apps created using AI, low-code, and no-code development platforms don’t stay that way
People Leaving the Organization
As apps and automations are built there may be missing rules for assigning ownership after they leave; creating blind spots for IT and security
Understanding Viral Apps
When apps are built from all corners of the organization, it is a challenge to know which are critical, creating guesswork for how to prioritize
Misconfigured Apps
Apps that do not function as intended can not only affect business operations, but are likely candidates to be leaking data
The solution
Keep business operations running smoothly
The Zenity platform enables continuous discovery of applications and automations and ensuring that things are running as they should be

Maintain Visibility
Maintain control and awareness of all apps and automations, even as they change hands and purposes
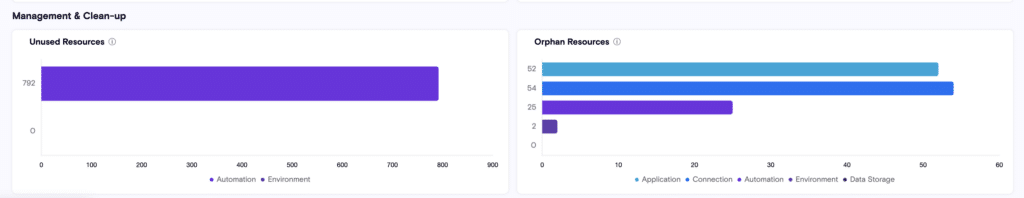
Detect Unused Resources
Apps that are no longer used can be security risks and cost-eaters
Real-time Governance
Mitigate business process failures in real-time through policies and playbooks
Efficient business operations. Strong security
By implementing strong security and governance to AI, low-code, and no-code development, business operations can run as intended.
Take Control
Audit the entire lifecycle of each application to keep track of apps as their purposes, owners, and users change
Maintain Operations
Swiftly and successfully resolve vulnerabilities from malfunctioning, orphaned or misconfigured apps
Drive Innovation
Securely empower all business users, even less technical ones, to create powerful apps and automations that can push the business forward
Stop Attackers
Find and fix apps that harm other processes or apps and/or that can be targeted by attackers as the weak link in the supply chain
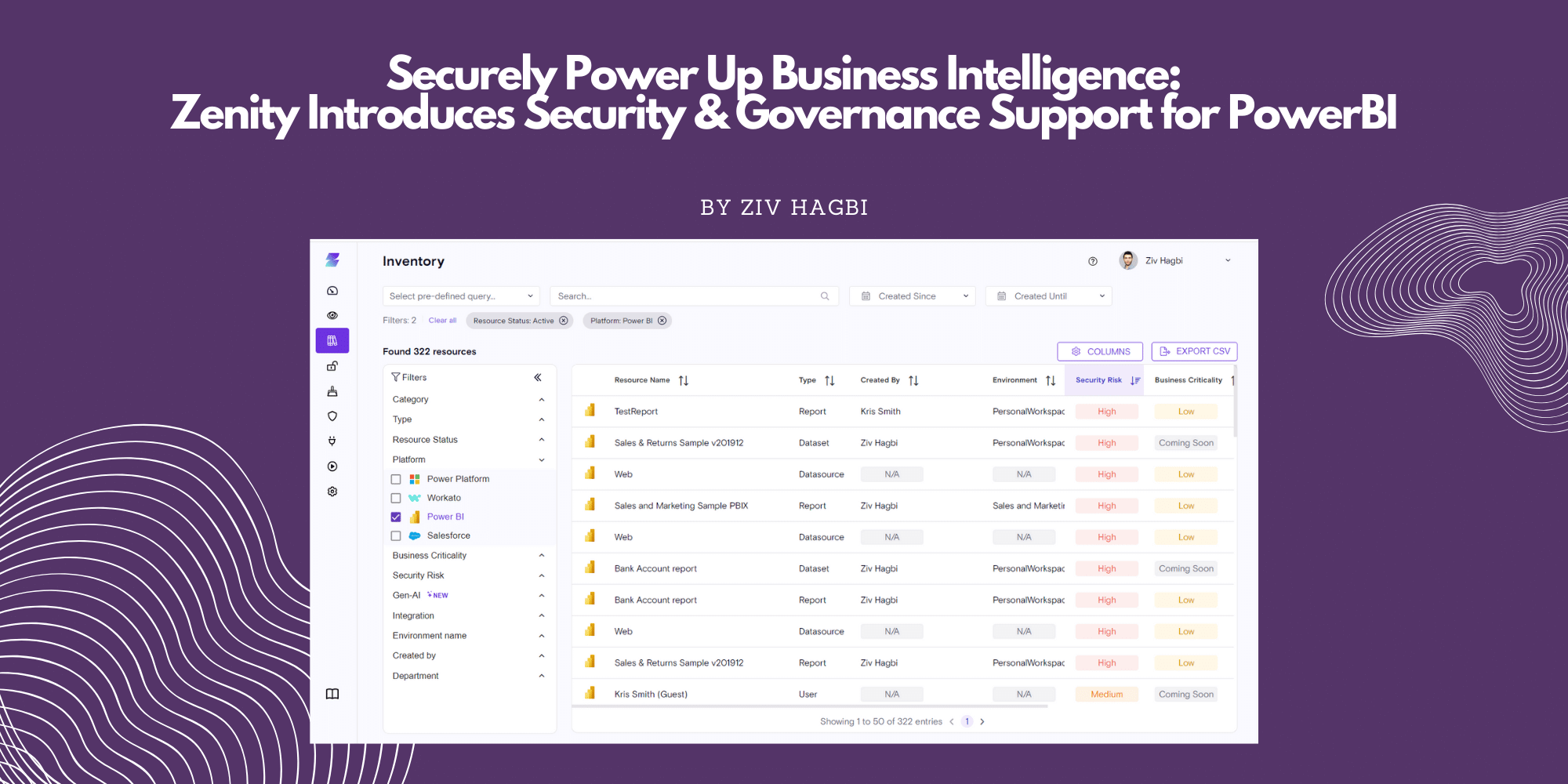
Securely Power Up Business Intelligence: Zenity Introduces Security & Governance Support for PowerBI
Want to learn more?
We’d love to hear from you and talk about all the latest updates in the world of low-code, no-code, and Al led development