salesforce
Security and Governance for Salesforce Development
Salesforce is now a full-fledged development platform, including robust AI capabilities, app builders, and more


The pROBLEM
As Salesforce grows, what security risks emerge?
While Salesforce has security controls for the platform itself, Zenity layers on security and governance for apps, automations, and connections built on top
Speed of Development
Professional and citizen developers create apps, reports, and more without any sort of SDLC, resulting in shadow development
Data Leakage Risks
Apps and automations push and pull data from non-Salesforce systems, creating easy ways for data to leak
Data Warehouse Storage
Salesforce’s Einstein AI introduces a huge data warehouse that must be managed
Supply Chain Risks
Connectors, add-ons and extensions are easily integrated into apps, with no oversight on what these are
The solution
Empower everyone to build useful apps and automations
Zenity’s security governance platform makes it so that Lightning App and Flow Builder, MuleSoft, IDEs, Apex, Einstein AI and more are not leaking data

Visibility at Scale
Continuously maintain cross-platform inventory of all low-code/no-code apps, automations, and integrations
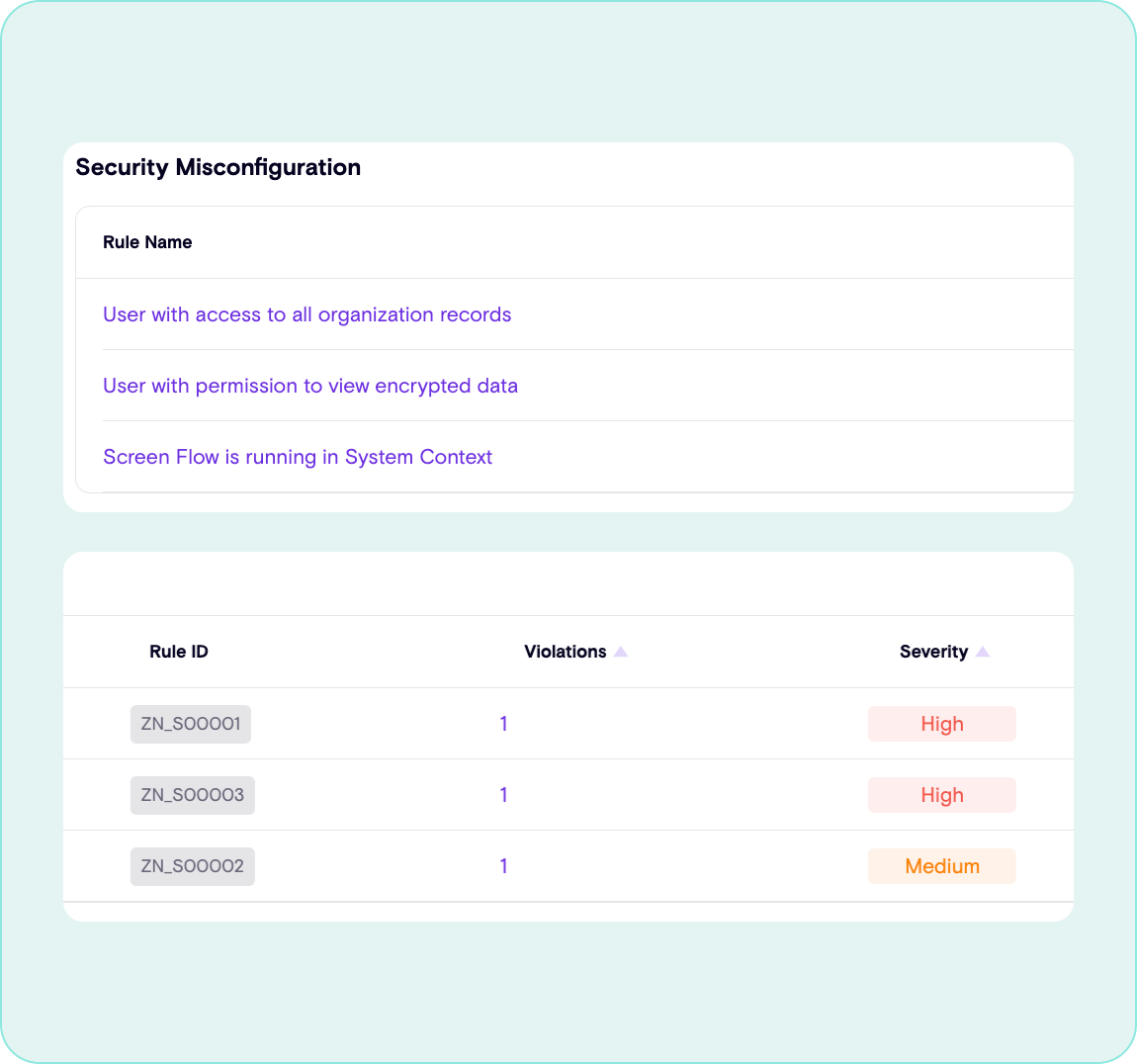
Vulnerability Management
Arm security teams with insights on where hard-coded secrets live, which reports and apps are over-shared, and more
Real-time Governance
Automatically mitigate risk in real-time with enforcement playbooks and customizable policies to ensure secure development
The benefits
Confidently secure Salesforce development
With Zenity, professional and citizen developers can harness the power of AI to get more done and process more data while maintaining security


Continuous Scanning
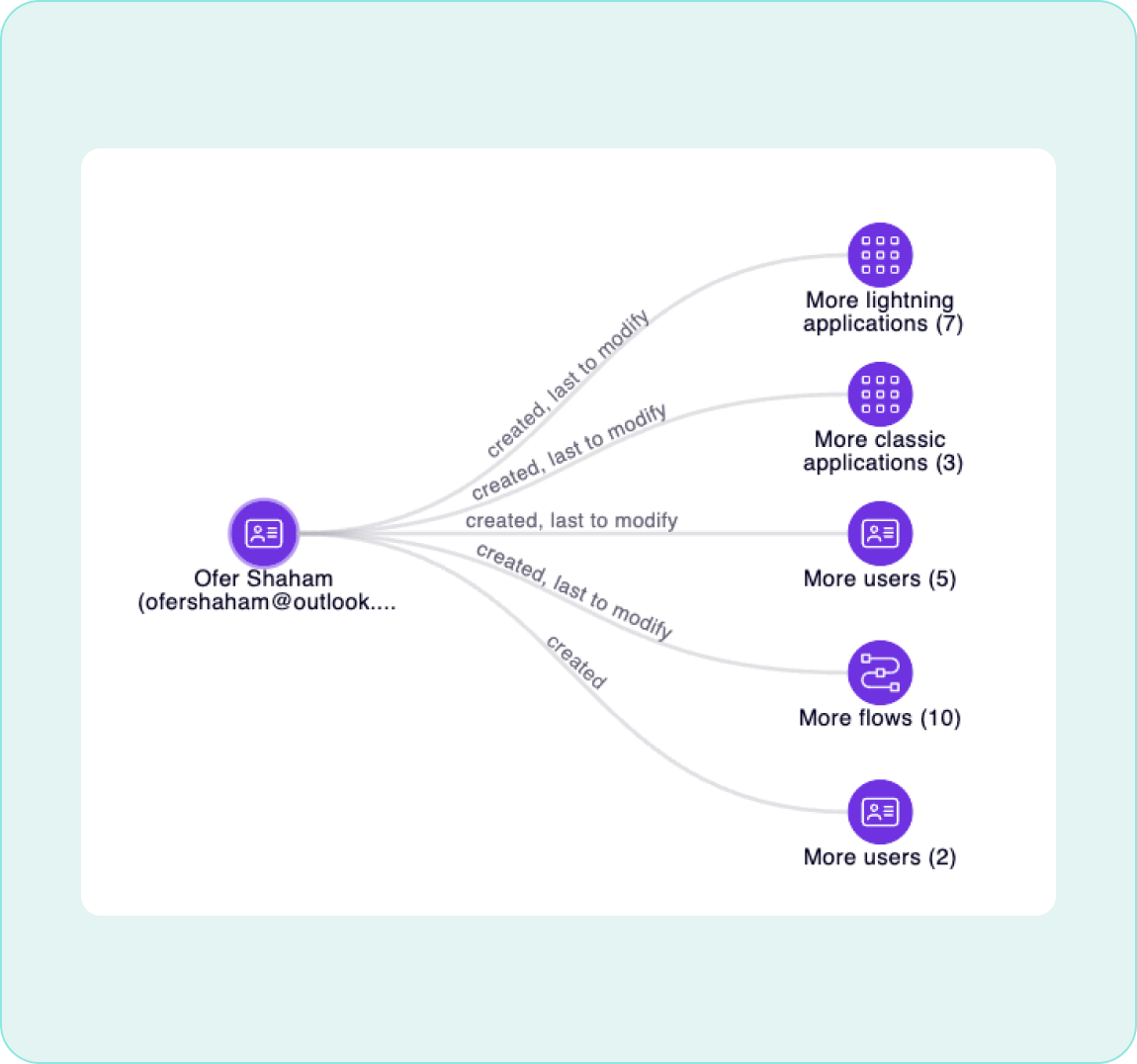
Scan Salesforce environments to maintain visibility of who is creating what, in real-time

Map Data Flows
Detect risky relationships between apps, users, data, and third-party components

Implement Governance
Leverage automated playbooks to take action when security vulnerabilities are detected and implement guardrails for secure development

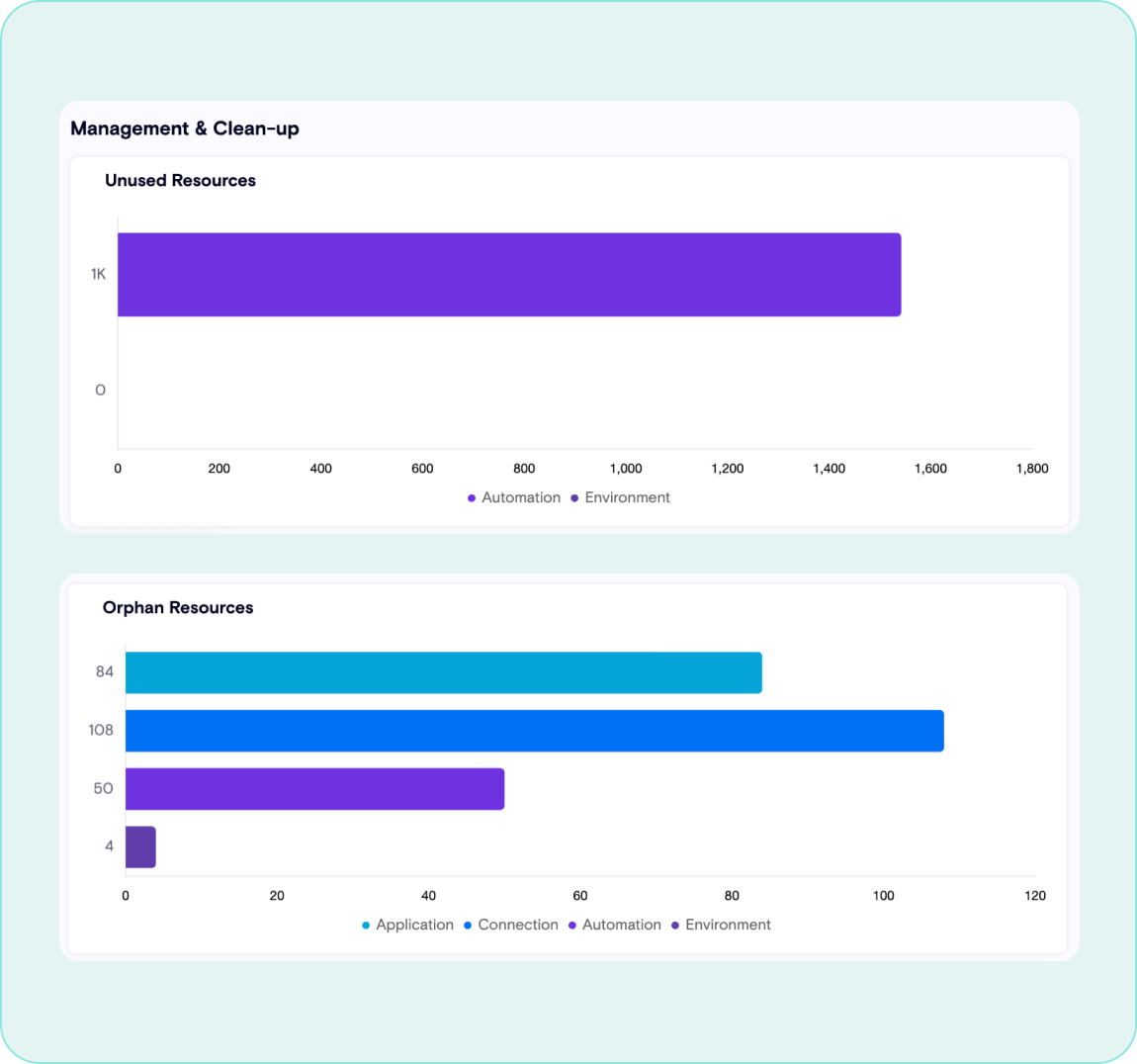
Maintain Hygiene
Identify unused or unowned resources that can eat up license costs and be blind spots for security teams
Want to learn more?
Subscribe to our monthly newsletter to stay up-to-date on all the latest updates in the world of
low-code/no-code development