Unlocking Supply Chain Transparency for Low-Code/No-Code Apps with SBOM

Introduction
The world of software development has witnessed a significant transformation thanks to low-code/no-code development platforms like Microsoft Power Platform, Salesforce, and ServiceNow. These platforms have empowered developers and business users of all technical backgrounds to create applications, automations, bots, connections (and more), rapidly and with greater accessibility. However, this newfound agility and democratization comes with an inherent challenge – the increased risk of security vulnerabilities stemming from third-party dependencies. Noteworthy incidents, such as the SolarWinds attack, have underscored the critical need for organizations to account for all software components within each application and its respective building platform.
The SolarWinds breach serves as a stark reminder of the vulnerabilities that can arise when an application incorporates third-party code without rigorous validation for potential vulnerabilities. In this rapidly evolving landscape, it’s crucial to address these challenges effectively.
The Role of Software Bill of Materials (SBOM)
Recognizing the pressing need to mitigate these risks, the US government has mandated the use of a ‘Software Bill of Materials’ (SBOM) as an industry-standard solution. SBOMs provide organizations with a comprehensive inventory of all software components, both first-party and third-party, including direct and transitive dependencies. This inventory is invaluable for identifying and managing risks effectively, reducing the threat of supply chain attacks.
Why SBOM Matters for Low-Code/No-Code?
Low-code/no-code platforms empower business and professional users to engage in advanced customization by obfuscating code, but often involve classic code that lies within the platform itself. Users can either code directly within the platform or import code from external sources, often without validating or testing it for vulnerabilities. This practice significantly increases the likelihood of unknowingly incorporating vulnerable third-party packages into applications, and organizations that lean on low-code platforms should be able to round out their security and compliance programs with robust SBOMs.
Two Key Use Cases of SBOMs
Within low-code/no-code platforms, there are two primary value adds:
- Inventory: SBOMs offer a comprehensive and accurate inventory of all software components, ensuring a holistic view of potential risks, including those posed by third-party dependencies.
- Known Risk Identification: By mapping out first-party and third-party dependencies, SBOMs allow users to identify existing vulnerabilities in two essential ways. First, they help pinpoint vulnerabilities in existing code, such as legacy JavaScript packages that haven’t been patched. Second, they assist in identifying the use of newly discovered Zero-Day vulnerabilities within apps and automations built using low-code/no-code platforms.
Collaboration with OWASP Cyclone DX Community
We are proud to highlight our collaboration with the OWASP Cyclone DX community, a full-stack Bill of Materials (BOM) standard that provides advanced supply chain capabilities for cyber risk reduction, which has also enabled the integration of a Low-Code/No-Code SBOM solution into the Cyclone DX format. This integration ensures that the broader software security community can harness the benefits of this innovative approach to enhance their supply chain security.
Zenity’s Unique Offering
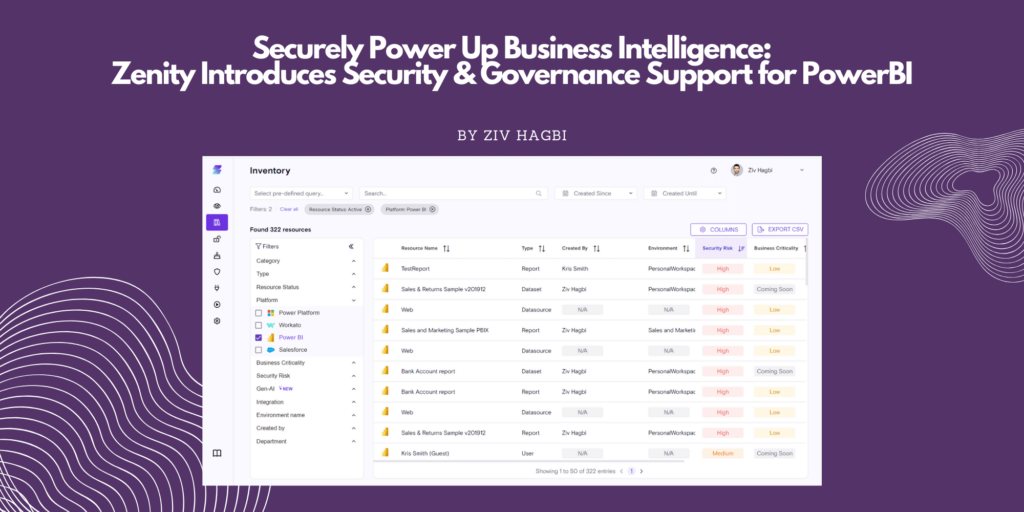
Zenity is addressing the supply chain security challenges for Low-Code/No-Code platforms by introducing the first SBOM for low-code/no-code development platforms. Our SBOM inspection mechanism dives deep into every code component, deducing the code libraries used within the application.
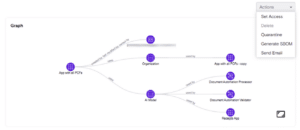
The Zenity SBOM solution seamlessly integrates with all Low-Code/No-Code development platforms, performing automatic scans of applications and generating comprehensive inventories of all components. As such, security leaders, auditors, and platform administrators gain a profound understanding of each application and can export this information to other internal systems, such as a centralized repository, for compliance purposes. Furthermore, the Zenity platform enables users to stream SBOMs to recognized scanners, which is particularly useful for companies employing centralized solutions.
Call to Action
Are you ready to fortify the security of your Low-Code/No-Code applications with SBOM? We invite you to contact our team for a demonstration or more information on how Zenity’s SBOM solution can safeguard your applications and supply chain.