Securely Power Up Business Intelligence: Zenity Introduces Security & Governance Support for PowerBI
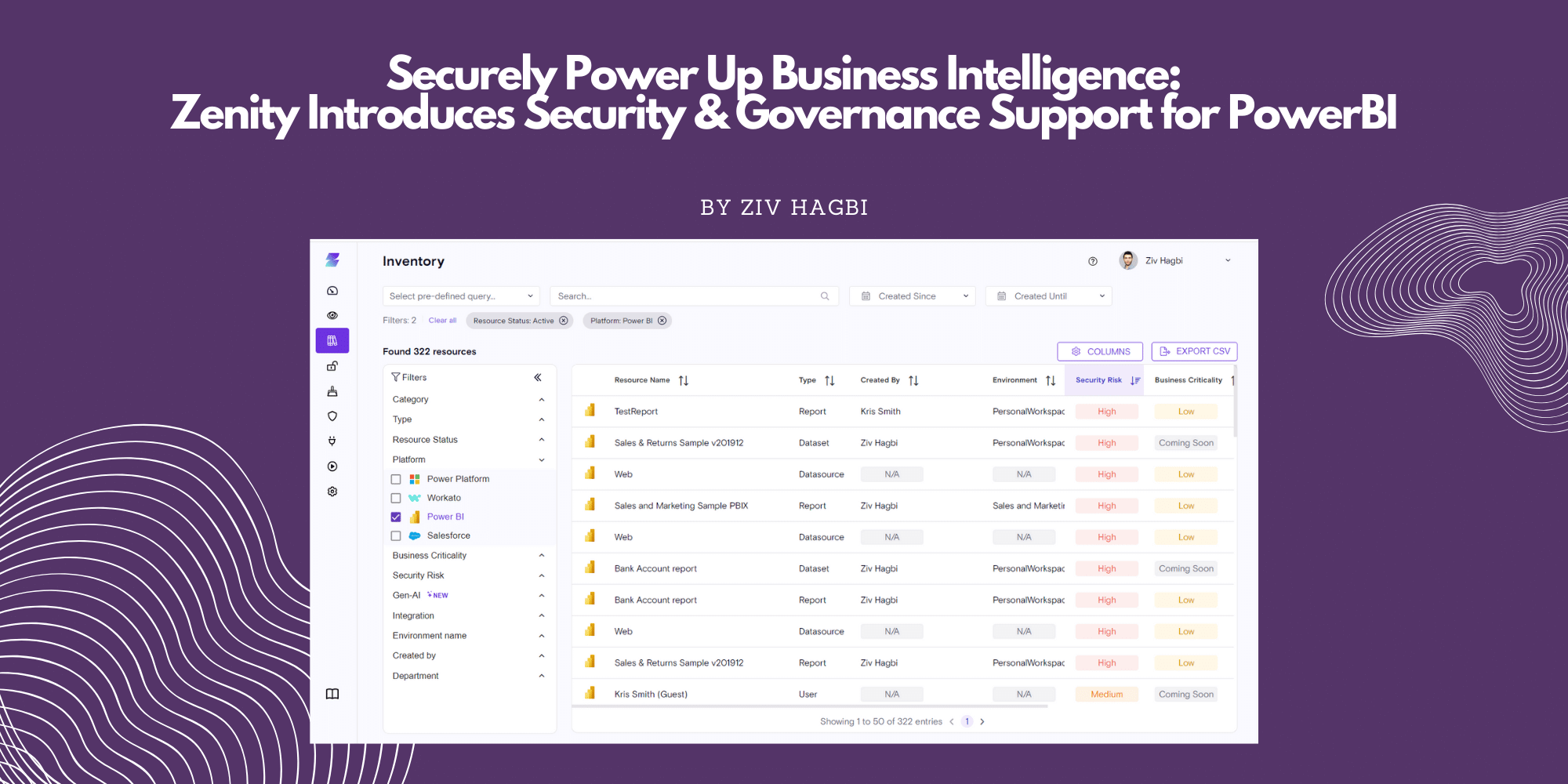
Businesses of all shapes and sizes are leveraging Microsoft Power BI to find insights within their own data. This standalone tool (not a part of Power Platform, despite its name) has emerged as a powerful tool, empowering all business users, not just trained data scientists, to transform raw data into meaningful insights. From data visualization to interactive dashboards, Power BI has become a cornerstone for decision-making across industries. However, as organizations harness the capabilities of this robust platform, it’s crucial to be aware of the cybersecurity risks that come with end users being able to build their own reports, dashboards, tables, and more.
What End Users Leverage Power BI For
It is important to note and understand the functional use cases of what makes Power BI so powerful.
- Data Visualization and Dashboarding: Power BI enables end users to create compelling visualizations and dashboards turning complex datasets into easy-to-understand graphs, charts, and reports. Whether it’s sales trends, market analysis, or operational metrics, Power BI allows users to present information in a visually appealing and comprehensible manner.
- Data Analysis: Power BI’s data analysis capabilities empower end users to explore data in-depth. With features like Power Query and DAX (Data Analysis Expressions), users can clean, transform, and analyze data to extract valuable insights, fostering a deeper understanding of business processes.
- Collaboration and Sharing: Power BI facilitates collaboration by allowing users to share reports and dashboards securely. This collaborative environment enhances communication within teams, as stakeholders can access and contribute to shared analytics projects.
Power BI also seamlessly integrates with other Microsoft tools and a variety of data sources, making it versatile and adaptable to diverse business environments. Users can pull in data from Excel, Azure, SQL Server, and many more sources, providing a holistic view of organizational data.
The Risks
The primary cybersecurity concern is the risk of data breaches. As business users are building dashboards, analyzing data, and collaborating, security leaders are likely to lose deep visibility as to who has access to which dashboards and data, where that data is flowing to and from, which guest users have access, and what is the overall exposure to sensitive reports.
Think of an end user who’s tracking operational metrics in a dashboard to track performance of a sales team. In order to do so, they will likely need to pull data from sensitive reports, sales and pipeline information, financial records, and more, in order to tell a complete picture. While this is likely being built by a Power BI administrator, it can also be built by an operations professional, a C-level executive, or an outside consultant.
Beyond the fact that these people are inherently not security professionals, they are chartered with ensuring that only authorized users can access their various reports and dashboards, and need to implement strong authentication measures. Even if done correctly, the interconnectivity of PowerBI resources leave a lot of power in the hands of builders who knowingly or unknowingly have access to loads of sensitive data when building things in PowerBI. Despite the fact that Microsoft has security and governance programs like Defender and the Center of Excellence, these tools have very limited support within PowerBI and fall short in telling the full picture of what each individual resource that is built in PowerBI can do and what the ensuing risks are.
The Solution
Enter Zenity. The first platform built to secure and govern citizen development that is done on low-code platforms like Power BI. Security teams are increasingly leveraging low-code tools like Power BI to democratize development and allow more people, regardless of their technical backgrounds, to build powerful business apps, resources, and drive innovation from all corners. The challenge, as outlined above is there is very little visibility as far as these end users hard-coding secrets into reports, creating access gaps where end users can accidentally share the underlying datasource when sharing an application, sharing sensitive corporate data with guests, and even less in place to prove to security teams (and auditors) who has access to what with regards to reporting, dashboards, and datasets.
Zenity’s solution is built on three pillars that now offers full support for Power BI:
- Visibility: Identify resources as they are built, providing security leaders and practitioners with deep, business-level logic of what each dataset, report, dashboard, app, and more is, what data it interacts with, and who, in turn, can access that
- Risk Assessment: As professional and citizen developers build new resources, Zenity can assess the for risk, identifying which are overshared, which have improper authentication methods in front of them, and which are susceptible to leak data
- Governance: Implement proactive and autonomous playbooks to ensure that risk does not go unattended and that business users cannot create inherently risky resources.

Power BI has undoubtedly revolutionized the way organizations handle and interpret data, empowering end users to make informed decisions. However, with great power comes great responsibility, and organizations must remain vigilant in addressing cybersecurity risks associated with data handling. By implementing strong security measures, organizations can harness the full potential of Power BI while safeguarding their valuable data assets. As technology continues to advance, staying ahead of cybersecurity threats will be paramount in ensuring a secure and efficient data-driven future; come talk to us to learn how we can help!



