Citizen development and Generative AI makes it easier and faster than ever to create powerful business applications. Can your security team keep up?
Innovators and leaders trust Zenity




AI and low-code development make it easier and faster for users of all technical backgrounds to spur innovation, automate mundane processes, and craft efficient business processes.
It also creates new challenges for security
Similar to the public cloud, AI and low-code platforms secure the underlying infrastructure, but not the resources or data built on top
As thousands of apps, automations, and copilots are built, the risks of data being processed, accessed, or stored where it shouldn’t dramatically increases
Unlike traditional application development, does not incorporate dedicated times for testing, analyzing, and measuring the security of apps
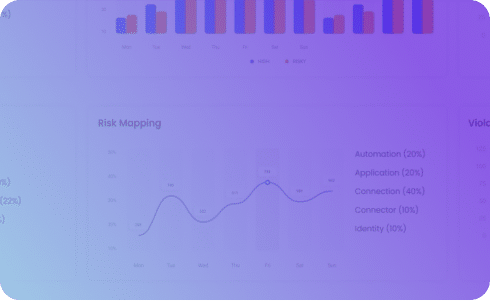
Unleash professional and citizen developers to safely create the things they need while meeting security and compliance standards

“Non-technical low-code/no-code users don’t follow app development security best practices, We had no visibility or control over the lowcode/no-code tools.”

“Varonis appreciates and prioritizes security measures at all times, in every aspect of our work.”
“….Securing the integrations and automations that people are building is a top priority for the company.”
Citizen development is a powerful business driver, but security and governance is needed to fully capture the value.

We’d love to chat with you about how your team can securely unleash citizen development