And That’s a Wrap on RSAC 2024

As we navigate through an era increasingly dominated by artificial intelligence, the theme of RSAC 2024, “The Art of the Possible,” couldn’t be more apt. This year, Zenity, a trailblazer in securing and governing business productivity tools like Copilot for M365, Power Platform, Salesforce, and ServiceNow, highlighted the vast possibilities—and the associated risks—of democratized technology and software development. Their insights into the potential and pitfalls of AI-driven business app creation underscored a pivotal shift in how we approach technology creation and management.

1. Securing AI Copilots: Navigating the New Frontier of AI Plugins at RSAC
The use of enterprise copilots is commonplace and was all the rage at RSA. Security leaders are put into a tough position where they’re stuck saying ‘no’ far more often than they’d like, and are even shutting down or drastically limiting these powerful business productivity drivers. The integration of AI into everyday business processes through Copilot for Microsoft 365 and others like it presents novel challenges and opportunities.
Heading into RSAC, Zenity introduced new AI Security Posture Management (AISPM) capabilities to allow enterprises to secure and govern Copilot for M365 and there was a lot of discussion around this. These discussions were a good sign for things to come. Security leaders are looking for ways to empower users with AI capabilities while ensuring these tools do not become backdoors for data breaches or compliance violations. The use of AI and enterprise copilots is almost forcing the business to work with security to ensure that innovation can properly be harnessed.
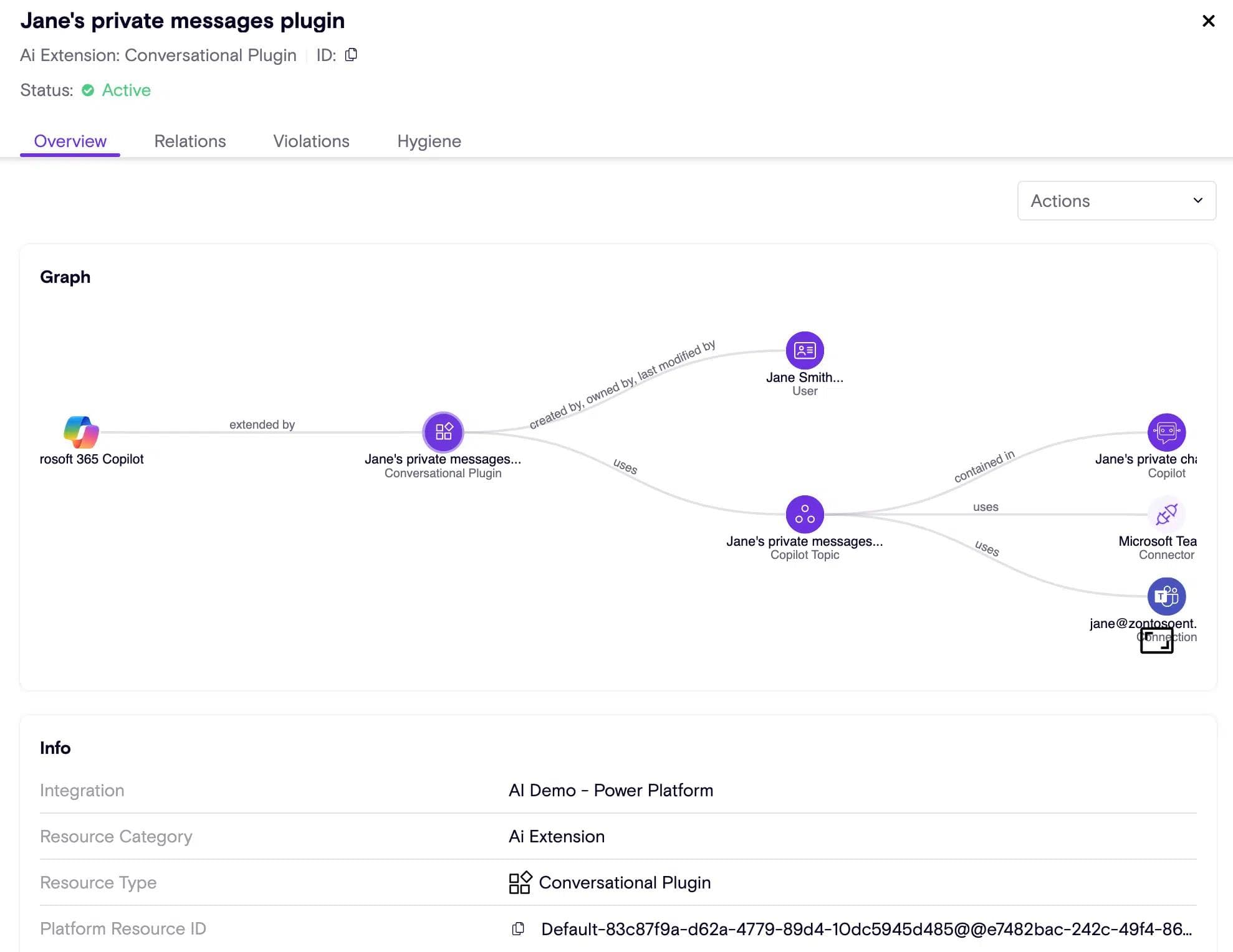
In order for teams to confidently unlock these tools, security leaders are looking for ways to:
- Detect and prevent sensitive data from going from end users to the LLM / AI model
- Ensure that people building and developing plugins (which are necessary to extend these copilots and read data in real-time) are doing so securely
- Prevent end users from unknowingly or maliciously side-loading these plugins into critical workflows that are then used throughout the business
The dual focus on functionality and security is critical as businesses increasingly rely on AI to automate complex tasks and generate insights. Zenity’s new capabilities are designed to monitor and manage how these AI plugins interact with sensitive data, ensuring that governance is not an afterthought but a foundational aspect of AI integration.
2. All You Need Is Guest: Simplifying Security in Low-Code Platforms

At RSAC 2024, Zenity CTO Michael Bargury shed light on a key aspect of LCNC platforms that often goes overlooked: the simplicity of integration and the inherent security risks it poses in his presentation “All You Need is Guest.” Drawing on recent explorations, such as the vulnerabilities discovered in Microsoft’s Power Platform, Michael articulated how seemingly benign features, like the ability to copy and paste data across different apps, easily bypass data loss prevention protocols. This functionality, within tools like Power Platform, while designed for ease of use and efficiency, unintentionally opens doors to potential data leakage. The most striking part of his research, which started last year and continues today, was the fact that this mechanism exists in every M365 tenant today:
- Power Platform is pushing hard on citizen development – the powerful concept of having every corporate user be an app creator.
- To build a useful app users plug in their credentials to any enterprise system (say SQL server) to integrate it with Power Apps.
- Other users who got access can now use those credentials, fully impersonating the connection’s creator. They do not get access to the actual secret, but they can perform any action facilitated by Microsoft infra. There are no logs, no way to distinguish the original user from others who got access.
This is all up to user choice and admins have no say or visibility in the matter. It’s up to security teams to seek out this visibility and assess these environments for risk. Michael’s talk advocated for a balanced view where ease of use does not compromise security. There simply must be an emphasis on the importance of understanding that every user, whether a guest or a core team member, interacts with the platform under certain security constraints. This perspective is crucial as it calls for a design philosophy that inherently includes robust security measures without burdening the user experience.
3. Addressing Data Leakage in Business Productivity Tools
Data leakage remains a pressing concern in the context of business productivity tools, like low-code development platforms and enterprise copilots. Zenity’s insights at RSAC 2024 highlighted that the very features that make LCNC tools accessible and powerful—such as drag-and-drop interfaces, AI copilots, and integration capabilities—also make them vulnerable to data breaches. Without proper oversight, these platforms can easily be misused, either inadvertently or maliciously.
Zenity argues for a proactive security strategy that includes real-time monitoring and intervention capabilities. By implementing comprehensive security frameworks and educating users about potential risks, companies can significantly mitigate the risk of data leakage. This proactive stance is essential in fostering a secure yet innovative development environment.
Finally, Zenity addressed the broader trends in low-code development and the increasing integration of AI. As these platforms evolve, they become not only faster and more user-friendly but also more complex in terms of the potential for errors and security vulnerabilities. The democratization of app development means that more individuals without a technical background can build applications, which while innovative, also increases the likelihood of mistakes and oversight in security practices.
The inclusion of AI accelerates these capabilities but also amplifies the risks. Zenity’s focus is on creating tools and protocols that ensure these powerful technologies are used wisely and safely. They advocate for a culture of continuous education and improvement that keeps pace with technological advancements, ensuring that every user, regardless of their technical skill, understands the implications of the tools at their disposal.
RSAC 2024 Conclusion
Our conversations at RSAC 2024 emphasized not only the transformative potential of AI and LCNC platforms but also the critical need for robust security frameworks that keep pace with this rapid evolution. As we step into the future, “The Art of the Possible” should also encompass the art of responsible and secure innovation, ensuring that the tech-enabled solutions we embrace do not compromise our data integrity or our ethical standards.
All ArticlesRelated blog posts

Inside the Movement Defining AI Security: AI Agent Security Summit Now On-Demand
I’m still buzzing from the AI Agent Security Summit in San Francisco just a few weeks ago! From hallway discussions...
The League Assembled: Reflections from the AI Agent Security Summit
At the AI Agent Security Summit in San Francisco, some of the brightest minds in AI security and top industry leaders...

Key Takeaways for Partners from the Zenity AI Agent Security Summit
Having joined visionary leaders and top practitioners at ZenityLabs’ AI Agent Security Summit in San Francisco,...
Secure Your Agents
We’d love to chat with you about how your team can secure and govern AI Agents everywhere.
Get a Demo