Why Are Low-Code Platforms Becoming the New Holy Grail of Cyberattackers?

Why Are Low-Code Platforms Becoming the New Holy Grail of Cyberattackers?
Low-code/no-code platforms for enterprise are booming. With more and more critical business assets now stored and handled by these platforms, it is essential to understand that low-code often leads to a large attack surface. This article will explore low-code/no-code from an attacker’s perspective to better understand their potential weaknesses and showcase why they are becoming the new holy grail for cybercriminals.
Essentially, it’s about identity and data
For low-code/no-code platforms to be effective in business, they have to make use of critical business data. This data could be on the cloud, on-premises, or even stored with third parties such as a trusted SaaS vendor. The low-code/no-code applications an organization uses must have access to these assets and interact with the data in order to function.
For example, let’s take a simple automated process where you send a slack message to a specific internal channel when you get a new message from a client. This basic process alone needs access to 2 critical assets – your business email and Slack account.
Once you connect those accounts to your low-code/no-code platform, the connection remains active, ensuring the process is permanently active. Unlike traditional credentials use, the connection to the low-code/no-code platform is continual. Therefore your platform account could be considered an advanced credentials wallet.
You could easily compare this to a password manager on your browser. The only difference is your browser stores those credentials (only using them based on your interaction) while your low-code platform continuously runs code using them. Therefore, an attacker with access to your low-code platform can also run code using your credentials.
Unfortunately, there’s more to it than that. Low-code platforms allow users to share connections with one another. For businesses, this feature makes a lot of sense. Organizations often require individuals to collaborate with each other or perform org-wide operations.
The downside is an attacker might leverage this feature to impersonate other users in the organization. Low-code connections effectively act as wrappers around authentication tokens to other SaaS services, opening more doors for an attack to exploit within the organization.
Furthermore, it can allow attackers to evade detection. It is highly unlikely that current industry-standard security tools can even identify something is wrong, let alone mitigate against it. Therefore attackers can infiltrate undetected, performing a stealth attack where they exfiltrate your data record-by-record.
What a real-world low-code ransomware scenario may look like:
Intrusion (Initial Foothold)
First, the attacker attempts to access an organization’s low-code account. This could be due to a vulnerability within the low-code platform or, more likely, another entry point (password spraying, etc.). For example, Microsoft Power Platform is integrated into the 365 suite, meaning an account takeover results in immediate Power Platform account access.
Reconnaissance
Once they have access to a low-code platform account, the next step for an attacker is to map all the available connections. In this example, we’ll assume that the attacker gains access to the organization’s Google Drive.
Encrypting cloud files (data manipulation)
With access to your low-code/no-code platform account, the attacker can use your cloud storage connections to encrypt all of your data stored there. Here is a simple flow we’ve built showing a ransomware attack on Workato:
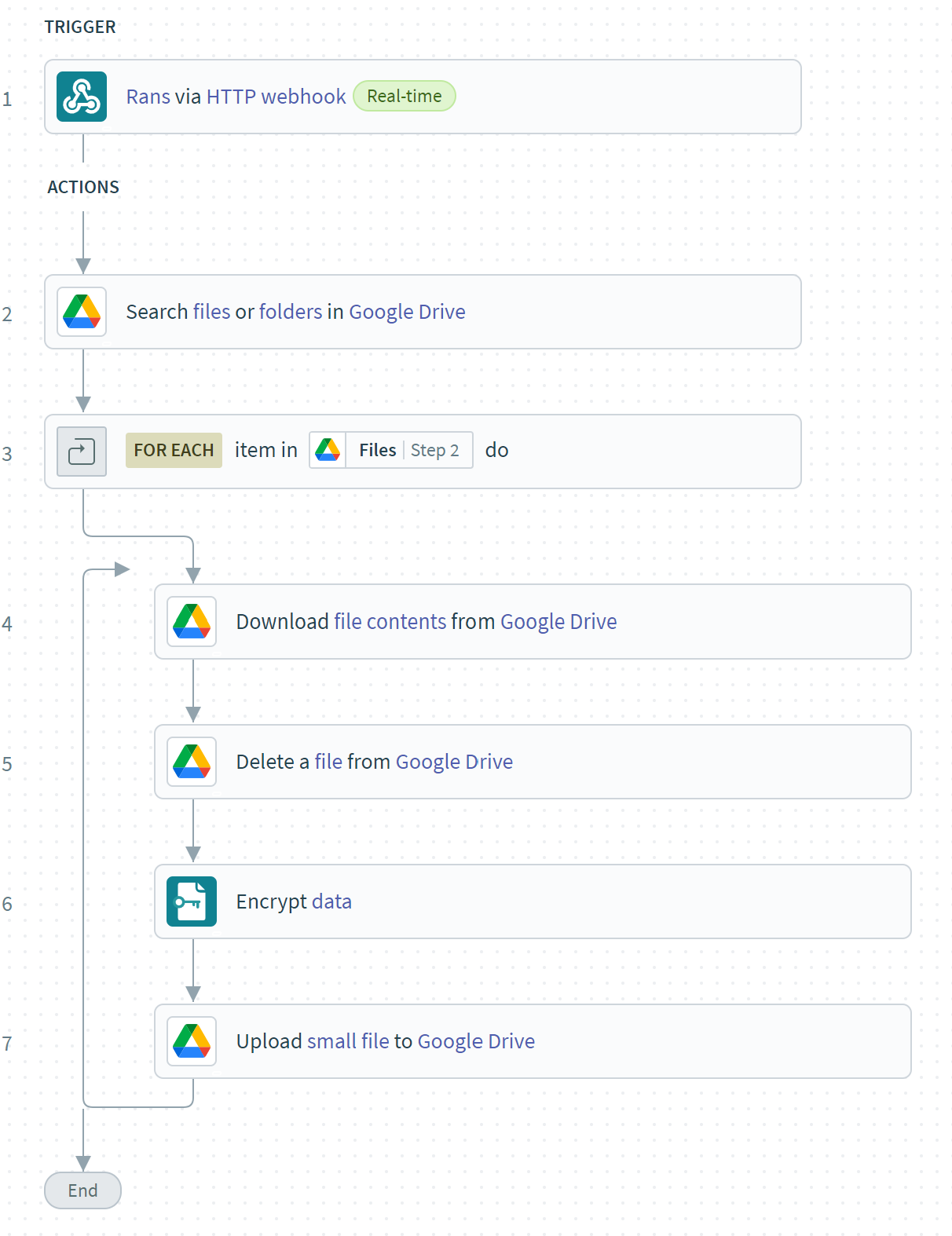
The Google Drive Data before running the ransomware:
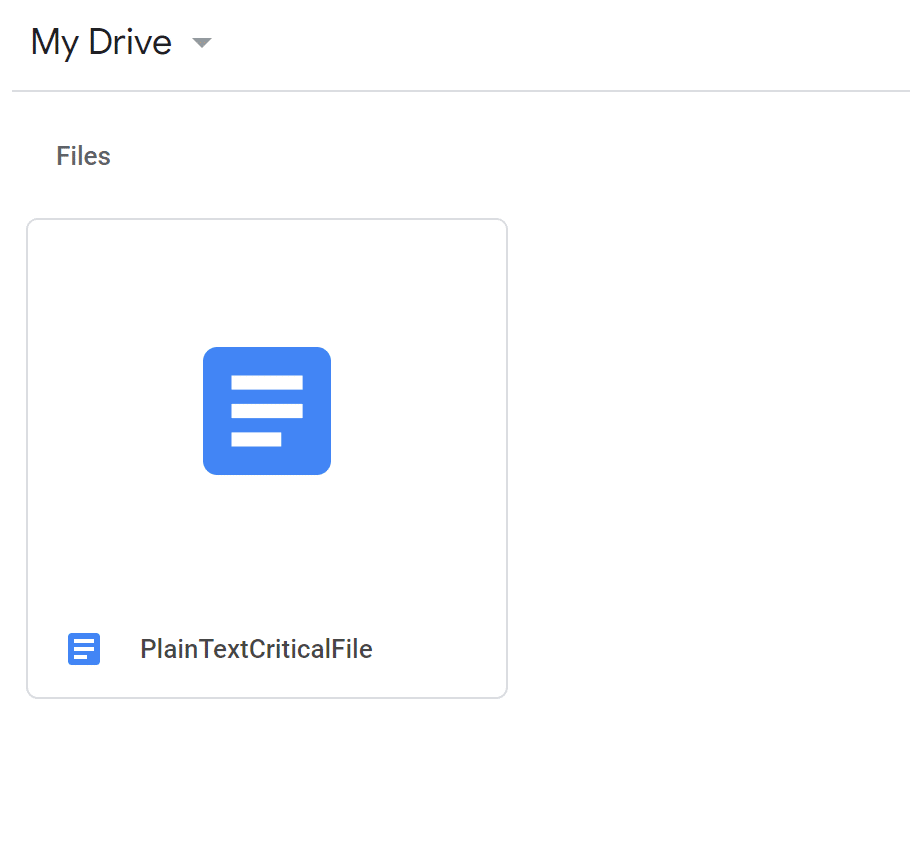
After running the ransomware:
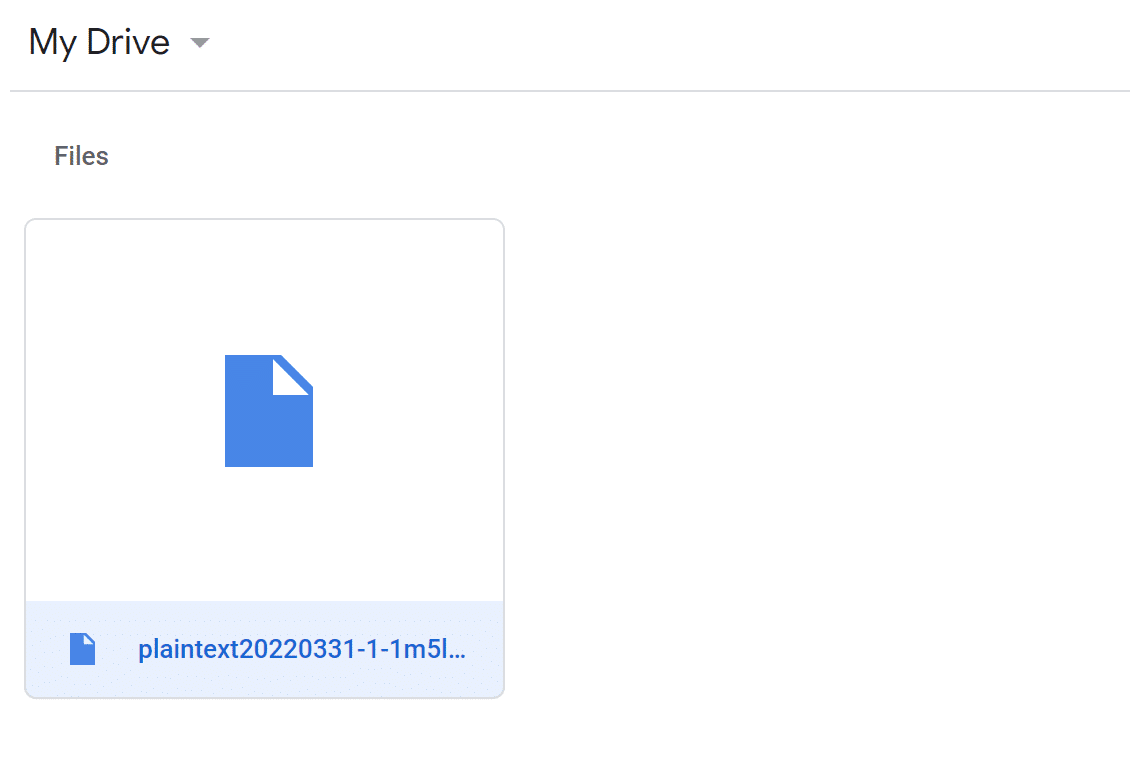
The file is now encrypted with the attacker’s public RSA key, and it can only be decrypted using the corresponding private key. Classic ransomware. Usually, the best remedy to a ransomware attack is to have a backup handy. However, the backup has become encrypted in this instance, leaving you scrambling for a solution.
It is essential to mention that encrypting files is one of many possible scenarios. Once inside, the attacker can read, write, or execute data as much as they like (within the context of the account and the connections shared with it). An intelligent attacker might choose to perform an ongoing silent attack, exploiting stealth to maintain access over an extended period.
Wrap-up
Low-code/no-code platforms are seeing widespread adoption with greater productivity for organizations and individuals. However, it is crucial to understand the significant security risks they pose.
Low-code/no-code offers new exploits for cybercriminals to target. As we’ve demonstrated, given the interconnected business environment we all operate in, threats can spread across organizations and escalate quickly.
It only takes a few simple steps for an attacker to go from low-code account access to taking over an organization’s cloud data. With access to company assets, low-code/no-code platforms are easily exploitable as advanced credential wallets.
In addition, the risks are amplified compared to traditional cloud risks since they are almost impossible to detect with ordinary off-the-shelf cyber security products.
It’s easy to see why low-code/no-code code platforms are the new holy grail for attackers.
Security professionals need to acknowledge the new and severe security risks to their organization from lowno code usage. While most security professionals have experience dealing with cloudweb and classic on-prem security, lowno code platforms act as new de-facto side-channels into an organization. Therefore, the new technology requires new considerations, and should not be overlooked.


